NIST Cybersecurity Framework - Summary & Guidance
The NIST Cybersecurity Framework is US Government guidance for private sector organizations that own, operate, or supply critical infrastructure. It provides a reasonable base level of cyber security. It establishes basic processes and essential controls for cybersecurity.
Contents
Overview of the NIST Cybersecurity Framework Cybersecurity process Detailed view of core controls Why should an organization adopt the NIST Cybersecurity Framework? Implementation tiers Other compliance mandates US federal agencies Additional informationOverview of the NIST Cybersecurity Framework
From process view, cybersecurity starts from understanding the organization, its mission, its risk tolerance. Part of this is understanding the organization's role in critical infrastructure. These are used to define roles, responsibilities, policies, and processes. Cybersecurity is realized as technical controls, monitoring, and planned responses. The processes are reviewed and improved based on experience.
From a technical standpoint, cybersecurity starts from managing identities, credentials, and their privileges and related access.
SSH is central in cybersecurity, because it is used in every data center for managing and securing networks, hardware, virtualization, systems, and/or data transfers.
Some of the most essential controls and SSH guidance are summarized in the following table. A more detailed listing of controls can be found later on this page.
| Control | Relating to | SSH Guidance |
|---|---|---|
| PR.AC-1 | Managing identities and credentials | In addition to users and passwords, SSH keys are access credentials and need to be managed. Many organizations have 10x more SSH keys than traditional users and passwords, and they often grant privileged access. SSH key management is an essential part of IAM and risk management. |
| PR.AC-3 | Remote access | Remote access must be properly managed and monitored. Encrypted protocols, such as SSH, Remote Desktop, or HTTPS, are typically used. Access should be monitored and tunneling back into the internal network from the outside should be prevented. |
| PR.AC-5 | Network integrity | A firewall should be used to protect the boundary and back-tunneling should be prevented. |
| PR.DS-2 | Data in transit | File transfers should use secure protocols. SFTP is the secure file transfer standard supported by all major vendors. SSH is the standard for remote system administration. CryptoAuditor provides auditability, analytics, and forensics capabilities for both. |
| PR.DS-5 | Protection against data leaks | Data Loss Prevention (DLP) systems should be deployed. Such systems should also monitor encrypted file transfers and terminal sessions. |
| PR.DS-7 | Dev/test separation from production | SSH key management needed as key-based access from dev/test to prod is a common finding. |
| PR.IP-3 | Configuration change control | SSH keys are part of security-related configuration, uncontrolled self-provisioning is not acceptable. |
| PR.MA-2 | Remote maintenance | All 3rd party connections should be monitored and access authorized according to process. |
| PR.PT-4 | Communications & control networks protected | SSH or SSL/TLS should be used to protect data transfers and control connections. |
| DE.CM-4 | Malicious code detected | Anti-virus systems should also inspect files inside encrypted protocols entering the organization. |
The role of SSH keys in access management has to be emphasized. Their use has become extremely prevalent, to the degree that they now constitute over 90% of all credentials in many organizations. Proper assessment and management of SSH keys is a critical priority. SSH keys are already being exploited by malware and hackers.
Cybersecurity process
The following diagram from NIST illustrates the Cybersecurity Framework process.
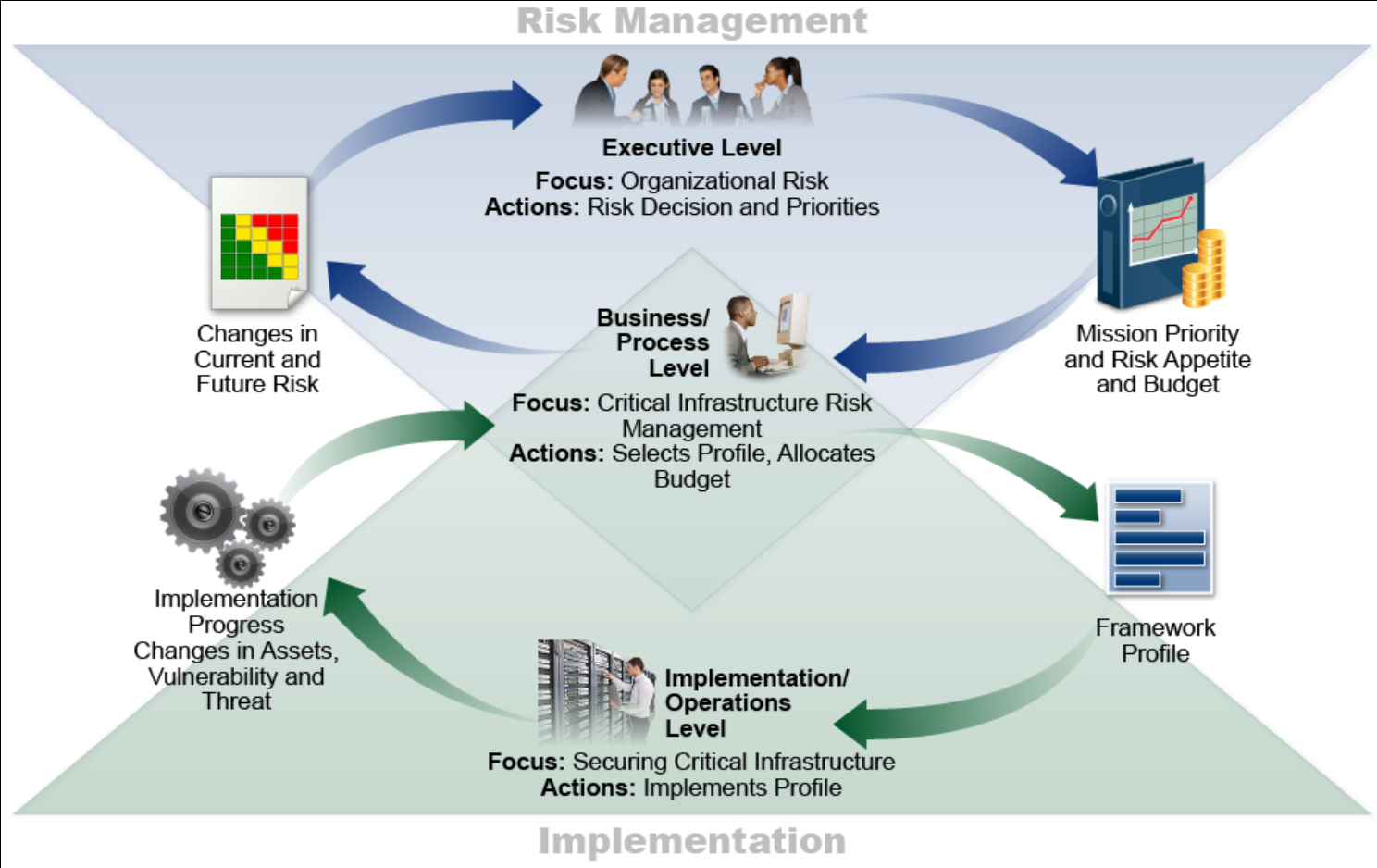
Detailed view of core controls
The framework provides core controls and processes in several areas essential to cybersecurity. It defines the five concurrent functions Identify, Protect, Detect, Respond, Recover. Several of these functions relate to processes and policies. The Protect function, in particular, relates to concrete protections that need to be implemented for systems and data.
Actual controls fall into a number of categories:
| Category | Explanation |
|---|---|
| Asset management (ID.AM) | Inventorying of devices, systems, software platforms, applications, external information systems; mapping organizational communications and data flows; prioritization of resources; definition of cybersecurity roles and responsibilities |
| Business environment (ID.BE) | Role in critical infrastructure and supply chain; mission priorities & resilience requirements; dependencies on other services; IS role alignment; legal and regulatory requirements understood and managed; governance and risk management processes address cybersecurity risks |
| Risk assessment (ID.RA) | Vulnerabilities & threats identified, documented, communicated, evaluated (impact & likelihood); responses identified and prioritized |
| Risk management strategy (ID.RM) | Processes, risk tolerance identified; consideration given to role in critical infrastructure |
| Access control (PR.AC) | Identities and credentials are managed for authorized devices and users; physical access is controlled; remote access is managed; permissions are managed (principle of least privilege, separation of duties); network integrity protected |
| Awareness and training (PR.AT) | Awareness and training, privileged user awareness, third party awareness, executive awareness, physical and information security roles training & awareness |
| Data security (PR.DS) | Data-at-rest protection; data-in-transit protection; formal asset management & disposal; capacity & availability management; protection against data leaks; integrity checking; separation of development and test from production |
| Information protection processes and procedures (PR.IP) | Compliance with policy & regulations; data destruction; continuous improvement; information sharing; response planning; response and recovery testing; HR processes (deprovisioning, personnel screening); vulnerability management |
| Maintenance (PR.MA) | Timely maintenance; control and monitoring over remote maintenance |
| Protective technology (PR.PT) | Log collection and analytics; removable media usage controls; access to systems and assets is controlled (incorporating the principle of least functionality); communications and control networks are protected |
| Anomalies and events (DE.AE) | Baseline established, detected events analyzed, multi-source data aggregation and correlation, impact determination, incident alert thresholds |
| Security continuous monitoring (DE.CM) | Network monitoring; physical monitoring; personnel monitoring; malicious code detection; unauthorized mobile code detection; external service provider monitoring; monitoring unauthorized personnel, devices, and software; vulnerability scans |
| Detection processes (DE.DP) | Roles and responsibilities, activities, testing, dissemination, continuous improvement |
| Response planning (RS.RP) | Response plan maintenance and execution |
| Communications (RS.CO) | Personnel roles, event reporting, information sharing, coordination with stakeholders, voluntary information sharing for situational awareness |
| Analysis (RS.AN) | Investigation of notifications, impact analysis, forensics investigations, incident categorization |
| Mitigation (RS.MI) | Containment, mitigation, documentation of acceptable risks |
| Improvements (RS.IM) | Incorporating lessons learned into response strategy, updating response strategies |
| Recovery planning (RC.RP) | Execution of recovery plan |
| Improvements (RC.IM) | Incorporating lessons learned into recovery plans and recover strategies |
| Communications (RC.CO) | Public relations management, reputation repair, communication of recovery activities to internal stakeholders, executives, management teams |
Why should an organization adopt the NIST Cybersecurity Framework?
The framework helps organizations understand, structure, manage, and reduce cybersecurity risks. Cybersecurity violations can cause substantial financial losses, damage reputation, or cause outages that may permanently damage a company's market position.
The framework assists in identifying the most important activities to assure critical operations and service delivery. It helps prioritize investments and provides a common language inside and outside the organization for cybersecurity and risk management.
US government defines critical infrastructure utilities (water and energy) and also other critical sectors such as financial services, transportation, communications, healthcare, food food supply, key manufacturers, chemical facilities, dams, and emergency services.
Implementation of the framework is currently voluntary. It is based on well-known standards and practices, and represents the best current practice in cybersecurity. However, each organization and industry will have to identify their special themes and topics to pay particular attention to. Most topics, however, are common to all sectors.
Implementation tiers
The framework defines tiers that describe the level to which the requirements are implemented. The tiers are sometimes referred to as maturity levels, but according to NIST they are more a tool for internal communication between cybersecurity risk management and operational risk management, and should not be seen as maturity level. Nevertheless, higher tiers represent higher degree of sophistication and maturity in the management of cybersecurity risks and responses.
| Tier | Name | Explanation |
|---|---|---|
| Tier-1 | Partial | Informal practices; limited awareness; no cybersecurity coordination |
| Tier-2 | Risk Informed | Management approved processes and prioritization, but not deployed organization-wide; high-level awareness exists, adequate resources provided; informal sharing and coordination |
| Tier-3 | Repeatable | Formal policy defines risk management practices processes, with regular reviews and updates; organization-wide approach to manage cybersecurity risk, with implemented processes; regular formalized coordination |
| Tier-4 | Adaptive | Practices actively adapt based on lessons learned and predictive indicators; cybersecurity implemented and part of culture organization-wide; active risk management and information sharing. |
Other compliance mandates
-
Many organizations combine Cybersecurity Framework application with COBIT.
-
Any organization accepting credit card payments must also comply with PCI, either themselves or by using a payment processor that handles compliance.
-
All US public companies are affected by Sarbanes-Oxley law; violations can result in criminal liability.
-
Energy companies are required to apply NERC CIP.
-
Health care and public health organization must adhere to the HIPAA security rule.
-
Financial institutions must consider Basel III and various other regulations.
All these regulations are fundamentally compatible with the cybersecurity framework. Some may provide additional requirements, or different emphasis, but for the most part they complement each other.
US federal agencies
Cybersecurity requirements for US civilian agencies are set by the FISMA law and NIST SP 800-53r4. For military and intelligence agencies, NSA establishes the requirements and guidelines.
Executive Order 13636 gives Federal Departments and Agencies the responsibility to aid in improving cybersecurity for critical infrastructure.

