Telnet – How to use
Telnet is one of the earliest remote login protocols on the Internet. It was initally released in the early days of IP networking in 1969, and was for a long time the default way to access remote networked computers. It is a client-server protocol that provides the user a terminal session to the remote host from the telnet client application. Since the protocol provides no built-in security measures, it suffers from serious security issues that have limited its usefulness in environments where the network cannot be fully trusted. The use of Telnet over the public Internet should be avoided due to the risk of eavesdropping.
Contents
Telnet Security Problems Eavesdropping Attack on a Telnet Connection Replace Insecure Telnet with Secure Shell (SSH) The Telnet StandardTelnet Security Problems
The Telnet session between the client and the server is not encrypted. Anyone with access to the TCP/IP packet flow between the communicating hosts can reconstruct the data that flows between the endpoints and read the messaging, including the usernames and passwords that are used to log in to the remote machine. This network attack requires very little expertise and can be performed with network debugging tools that are readily available.
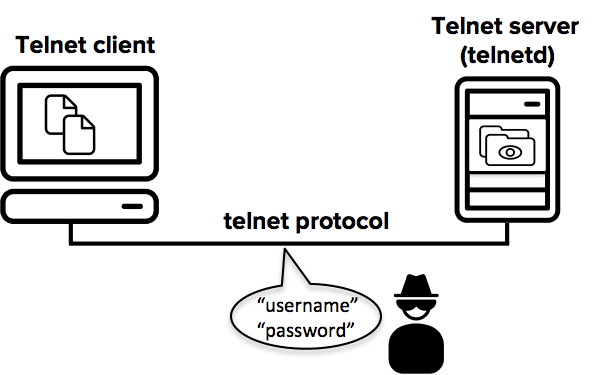
Packet sniffing attacks like the above were the underlying reason for developing SSH, and they were the most common security problem on the Internet already in the mid-1990s. Today mass monitoring and mass collection of credentials from the Internet by intelligence agencies, criminals, and hackers is routine.
Eavesdropping Attack on a Telnet Connection
The figure below presents a sample mock attack on an unprotected network protocol such as Telnet. Without encryption the data communications can be read by anyone that has access to the network packet stream.
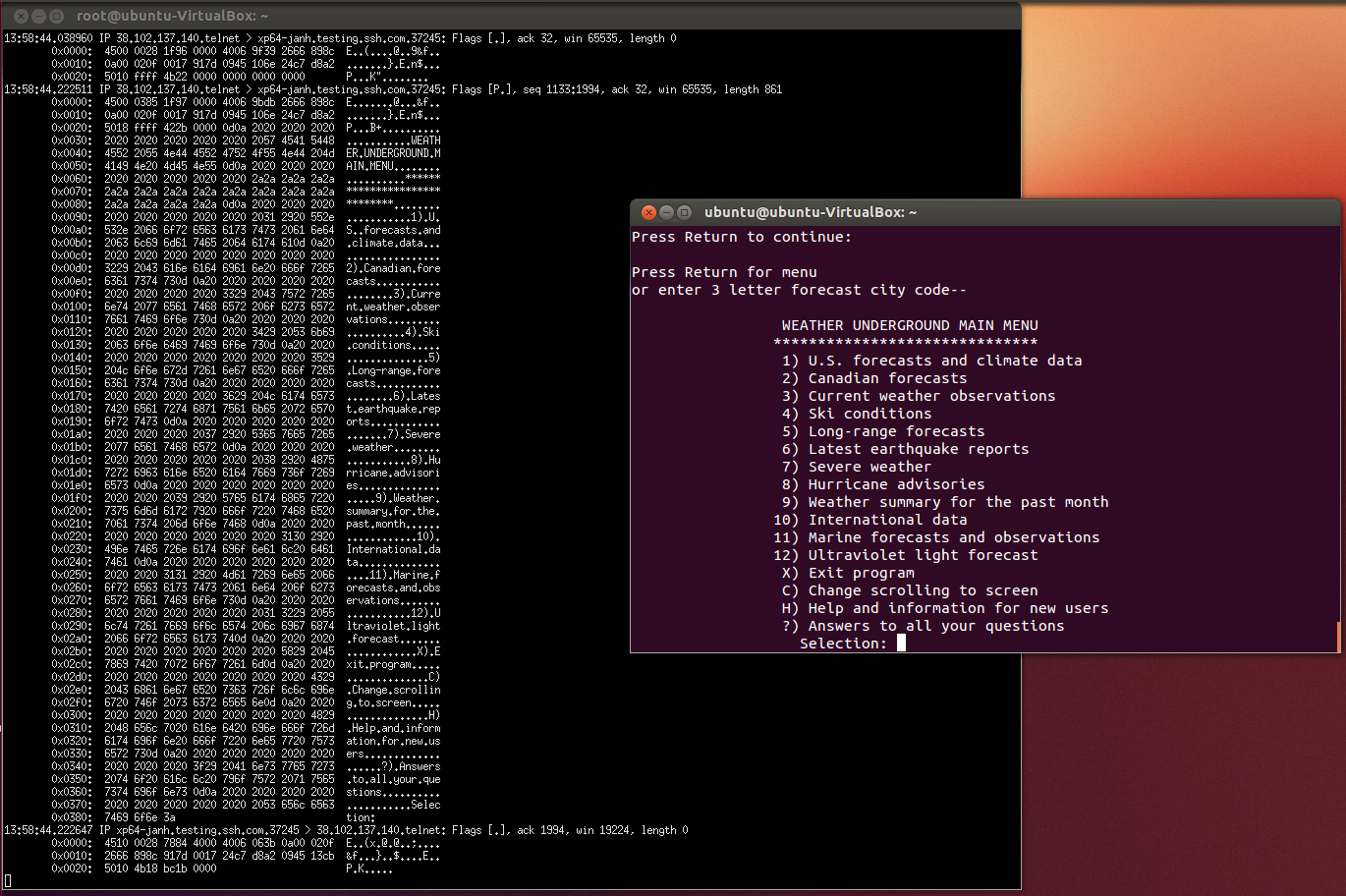
In the figure above the black terminal window is used to run a common network traffic analysis tool (tcpdump) while the maroon window is used to run a Telnet session to a weather information service. A closer look at the tcpdump window reveals that the contents of the Telnet session are easily readable from the traffic dump – as would be usernames, passwords, and other details if such had been transmitted.
Accessing any networked session like this exposes the users to identity, password, and data theft.
Replace Insecure Telnet with Secure Shell (SSH)
SSH (Secure Shell) provides a secure alternative to Telnet. SSH protects user identities, passwords, and data from network snooping attacks, and allows secure logins and file transfers.
SSH has practically replaced Telnet, and the older protocol is used these days only in rare cases to access decades old legacy equipment that does not support more modern protocols. And there are still organizations that simply do not care about security.
For Unix and Linux operating systems, the OpenSSH implementation comes free with the operating system and can be used to replace Telnet.
For Windows, z/OS, and for commercial support, see Tectia SSH.
Download Free SSH Client (Windows 7 and up)
The Telnet Standard
Telnet is a protocol specified by the Internet Engineering Task Force (IETF). The protocol is documented in RFC 854.

