Whether you are a regular Microsoft 365 user or a super admin wielding a lot of IT power, your secure password management. It just makes cybersecurity sense, and it is required by law.
But what is the best and most secure way for organizations to manage passwords that are especially powerful access credentials in the hands of administrators, developers, and consultants?
Contents
Challenges with password vaulting
Passwordless access without password vaulting
Better without password vaults
The conventional wisdom in the secure access space says that you should vault your passwords and rotate them. Password vaulting is what most privileged access management (PAM) solution vendors claim is the core of PAM, it is what most market analysts expect from PAM solutions, and it is simply what PAM vendors have been doing for the past 20 years.
But are there challenges with password vaults? There certainly are.
Challenges with password vaulting
1. Compromised passwords often fulfill compliance standards
A recent study investigating more than 800 million compromised passwords found that:
-
88% of passwords used in successful attacks consisted of 12 characters or less, with the most common being 8 characters (24%).
-
‘Password’, ‘admin’, ‘welcome’, and ‘p@ssw0rd’ were the most common terms. In short, very weak passwords.
-
83% of compromised user passwords were conventionally considered as "strong passwords", satisfying both length and complexity requirements of cybersecurity compliance standards such as NIST, PCI, ICO for GDPR, HITRUST for HIPAA, and Cyber Essentials for NCSC.
That last bullet point really hits home. A host of security professionals and cybersecurity standardization bodies recommend certain types of passwords, but a big chunk of them end up being compromised anyway. Will password vaulting really solve the proliferation of passwords?
2. The LastPass password vault breach
Let’s look at the infamous LastPass breach in which the popular password manager provider got hacked.
The LastPass hacker got hold of an engineer’s master password that granted access to the LastPass corporate password vault. With this, they were able to locate the decryption keys that opened the encrypted format of the customer password vault backups.
Even professional users get careless, and their endpoints can be compromised. A ‘regular’ compromised password can open a path to a password vault that, in this case, jeopardized the entire customer base of the company.
A passwordless dynamic access solution could have prevented this risk.
3. GitHub repository password leaks
According to recent research, software developers leaked over 10 million credentials and passwords in 2022 in GitHub commits. In practice, this means that the company IPR and its keys to the kingdom are being compromised all the time.
Again, it makes sense to question the traditional way of trying to solve such a challenge. GitHub is the global go-to place for software development, where developers collaborate on and manage code repositories, including production code. It is hosted in the cloud, and developers operate at cloud speed.
Is it a surprise that dynamic cloud environments and modern R&D methodologies, like DevOps, are sometimes a bad match with static solutions like password vaults?
Passwordless access without password vaulting
Passwordless authorization not only allows (privileged) access to critical targets without the need to vault and rotate passwords afterward but also reduces the risk of cybercrime by eliminating common attack vectors.
One of the most powerful ways to achieve this, while ensuring security and compliance, is by using an approach where the authorization to access a target is created just-in-time (JIT) with ephemeral certificates.
These certificates contain sensitive information (like a password) needed to access a target, but the privileged user never sees or handles any passwords. What’s more, the certificates expire automatically within minutes after access is granted, making access revocation automatic.
Learn how easy it is to manage access without passwords in our video >
In a modern solution, a Linux admin authenticates to a PAM solution, like PrivX, using biometric authentication, like a fingerprint. They then see only the targets available to them based on their role, click their chosen target, and just like that, they are in. No traditional login credentials at all.
This is possible because the home of identities (Identity and Access Management, IAM) is mapped alongside the home of roles (Privileged Access Management, PAM).
The neat thing is that the whole process is end-to-end passwordless - all the way from the identity to the role and the target. Password vaulting or rotation is simply no longer necessary. Neither are one-time unique passwords. That’s true Zero Trust.
Better without password vaults
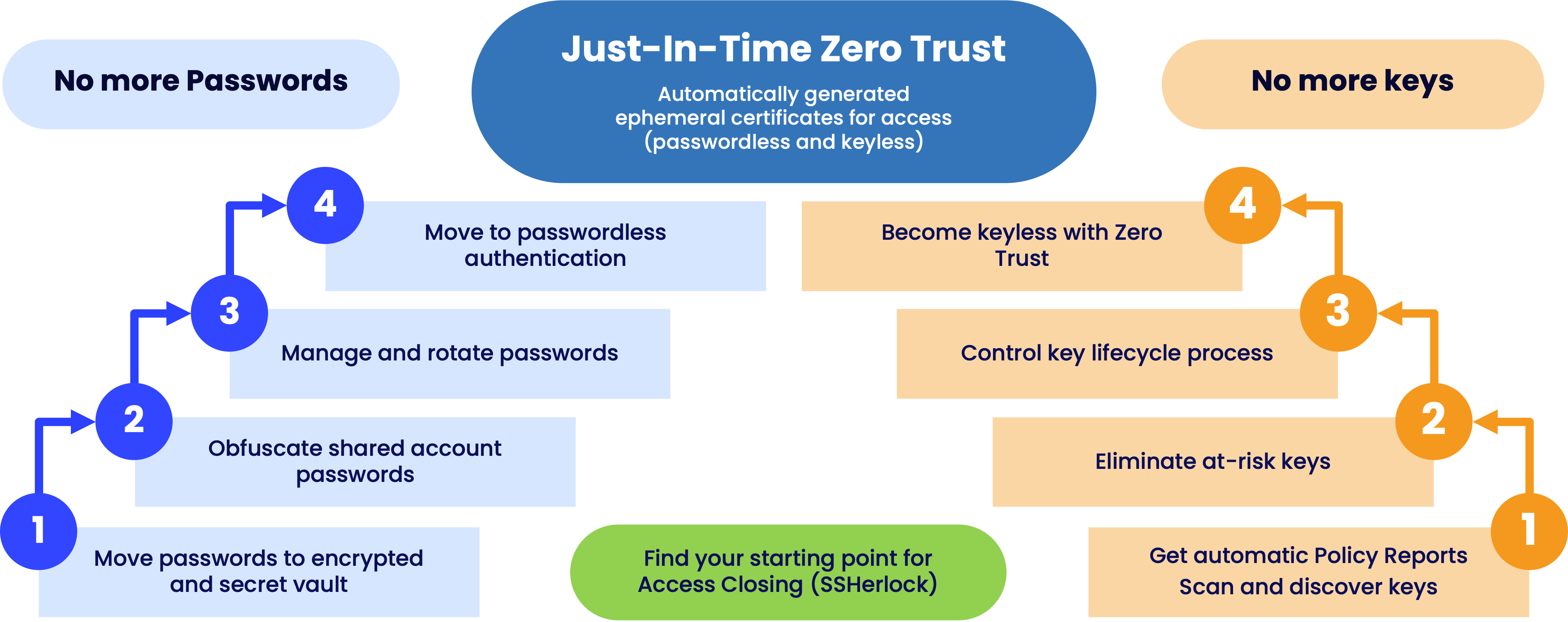
We at SSH Communications Security have been promoting passwordless authentication and authorization for quite a while. At the same time, we realize that it is nearly impossible to go all-in with passwordless at one go. Password vaults are needed for certain use cases due to technological and sometimes also policy constraints.
This is why we offer a path to passwordless, like in the image below, that you can embark on at your own pace:
And the solution that makes it all happen is our Zero Trust Suite. In fact, we suggest you manage your passwords AND keys from this single solution which gives you control over your credentials but also helps you get rid of them with a passwordless and keyless approach.
Learn more about the best way to manage encryption keys in this blog post >>>
FAQ
What issues can happen if I rely solely on password managers for my password management?
Relying solely on password managers can expose you to risks such as data breaches where centralized password data might be compromised, reliance on a single point of failure, and potential lockouts if the password manager service experiences downtime or you lose access to it.
Is two-factor authentication sufficient to ensure password security without a password manager?
While two-factor authentication significantly enhances security by adding an extra verification step, it may not be sufficient alone for total password security, especially against phishing or social engineering attacks. It's best used in combination with other security practices.
Can individual password management improve efficiency over using centralized password managers in multiple environments?
Individual password management can improve efficiency in scenarios where users need fast access without the complexities of centralized systems. It eliminates dependencies on third-party tools and networks, which can be advantageous in multiple environments with unique security requirements.
How effective is activity logging and email notifications in enhancing password protection without relying on password managers?
Activity logging and email notifications can significantly enhance password protection by providing real-time alerts about suspicious activities, enabling quicker response to potential threats. However, their effectiveness depends on proper setup and the user’s attentiveness to alerts.
Jani Virkkula
Currently employed by SSH.COM as Product Marketing Manager, Jani is a mixed-marketing artist with a strong background in operator and cybersecurity businesses. His career path of translator->-tech writer -> marketer allows him to draw inspiration from different sources and gives him a unique perspective on all types...