Plant-wide, global, or local IT/OT access control at industrial scale
IT and OT convergence refers to the integration of Information Technology (IT) and Operational Technology (OT) systems and data. Traditionally, IT systems focus on managing data for business operations, covering areas such as databases, networks, and applications.
OT systems, on the other hand, control physical processes and machinery in industrial environments, including manufacturing, utilities, energy, and other critical infrastructures. OT is responsible for monitoring, managing, and controlling physical devices like SCADA systems, PLCs, and industrial control systems.
While IT-OT convergence offers significant advantages, it also brings challenges, especially in securing legacy OT systems that were not originally designed to be connected to the internet. As a result, cybersecurity frameworks like ISA/IEC 62443 and NIST’s cybersecurity guidelines are increasingly being adopted to help manage the security complexities arising from IT-OT integration.
IT-OT convergence is basically integration of People, Process and Technology (PPT) requiring the following:
- A Governance Structure to determine how does the organization moves about solving cyber challenges
- Tools Implementation that enables monitor, measure and manage the cyber security threats
- Managed security portfolio which does continuous monitoring
- An awareness program, which provides continuous awareness to the users.
From data and & systems perspective, the convergence of IT and OT aims to enhance operational efficiency, improve data-driven decision-making, and foster stronger cybersecurity strategies. Some key aspects of IT-OT convergence include:
- Unified Data Analytics: By merging IT data with real-time OT data, organizations can gain insights that improve productivity, maintenance, and resource optimization across both digital and physical domains.
- Enhanced Security Posture: Convergence helps organizations implement holistic cybersecurity practices, as traditionally isolated OT systems are now connected to broader networks, making them more vulnerable to cyber threats.
- Operational Efficiency: IT-OT integration enables automation and predictive maintenance, reduces downtime, and enhances the overall efficiency of industrial operations through data sharing and streamlined workflows.
- Compliance and Governance: Convergence allows organizations to apply unified compliance standards across both IT and OT systems, simplifying regulatory adherence and policy management.
Overview of Convergence of IT-OT: Emergence of Industry 4.0
Convergence of IT and Industrial Automation historical steps are shown in the following picture (Source: IoT Analytics).
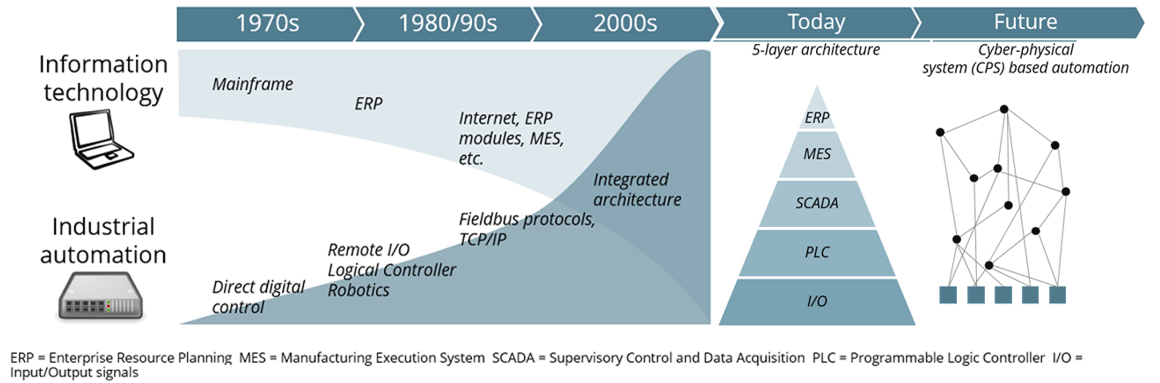
How IT-OT Convergence current and future states look like?
The next picture will show how the current and future stare look like and what are the most important gaps and remediation steps are needed to transform and converge IT and OT data and systems.
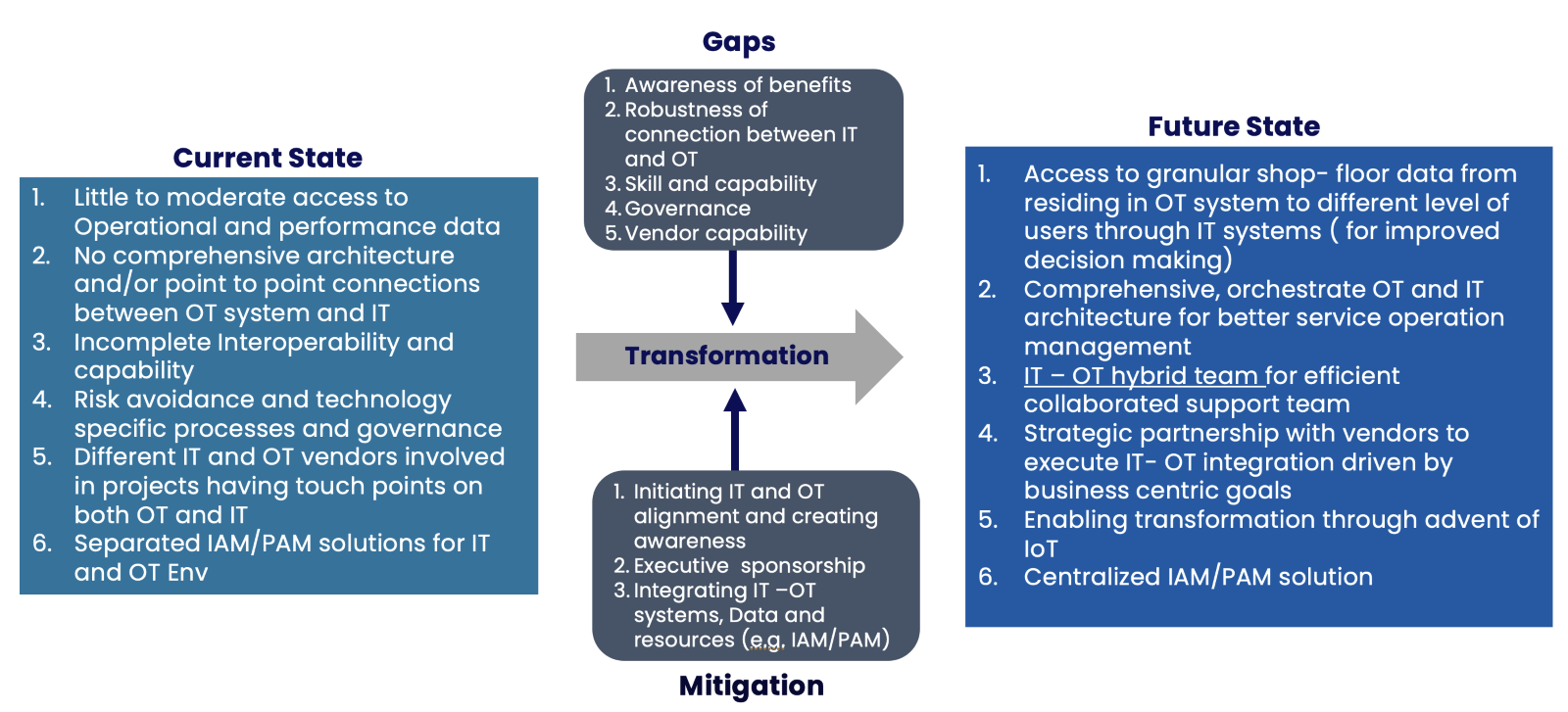
IT-OT Convergence best practices
Here are listed the most common IT-TO Convergence best practices based on standards, regulations, frameworks etc:
- The vision, strategy and execution of the business plan need to include security, reliability and safety. These should be part of the business planning process at all levels of the organization (regardless if you are an IoT solution provider or a customer)
- Security should be “owned” by one person at the executive level who is responsible for both IT and operations. Security policy, governance and end-user education need to extend across the IT and OT environments as systems are interconnected
- Technologies and threats across the IT and OT environments should be clearly understood. Technologies that work in the IT environment may not necessarily work in the OT environment. Additionally, threats may be different in the IT and OT environments
- A threat intelligence framework needs to be set up so that the organization can be up to date on the latest information on threats and be prepared to deal with them
- Baseline security controls should be deployed across all layers of the organization’s environments
- Regular risk assessments across all environments must be performed to identify vulnerabilities and ensure that the appropriate security controls are in place
- The organization and customers should consider NIST 800-5310 for IT and NIST 800-8211 and ISA/IEC 6244312 for ICS and OT
- Establish or update the security patch process to better address vulnerabilities. Follow the recommendations laid out in IEC 62443-2-3, which describes requirements for patch management for control systems
- Develop ICS-specific policies and procedures that are consistent with IT security, physical safety and business continuity
Most common access management challenges
Access management is essential for securing systems, applications, and data within an organization, but it comes with several common challenges:
- Balancing Security with Usability: Striking the right balance between security and usability is difficult. If access controls are too strict, users might seek workarounds that can introduce security risks. On the other hand, if access is too lenient, it increases the risk of unauthorized access
- Managing Diverse Access Levels: Organizations often need to manage a variety of access levels for employees, third-party contractors, and partners. Ensuring that each user has the correct level of access based on their role and responsibilities, and promptly updating or revoking access as roles change, can be challenging.
- Password Fatigue and Complexity: Users frequently experience password fatigue due to the need to remember multiple complex passwords across systems. This can lead to insecure practices like password reuse or storing passwords in insecure ways, which may compromise security.
- Monitoring and Auditing Access: Continuously monitoring who has access to what resources and auditing access logs to detect suspicious activity is vital but can be difficult to implement effectively. Many organizations struggle to keep up with access reviews, especially in large or complex IT environments.
- Managing Access in Multi-Cloud and Hybrid Environments: As organizations move to hybrid or multi-cloud environments, managing access across these diverse platforms becomes a challenge. Consistent policies and controls are required to manage access across on-premises, cloud, and third-party applications.
- Identity Sprawl: With more applications, systems, and third-party integrations, organizations often experience "identity sprawl" where identities proliferate across multiple platforms, making it difficult to centralize identity and access management (IAM) practices and creating potential gaps in security coverage.
- Compliance Requirements: Different industries and regions have unique compliance and regulatory requirements (such as GDPR, HIPAA, and SOX), which require strict access controls. Meeting these requirements often demands significant resources and close collaboration between security and compliance teams.
Organizations commonly address these challenges by implementing solutions like single sign-on (SSO), multi-factor authentication (MFA), privileged access management (PAM), and identity governance and administration (IGA) tools. These approaches help streamline access management processes while maintaining security across diverse systems and user roles.
Most common challenges for interactive and A2A access are shown in the next picture.
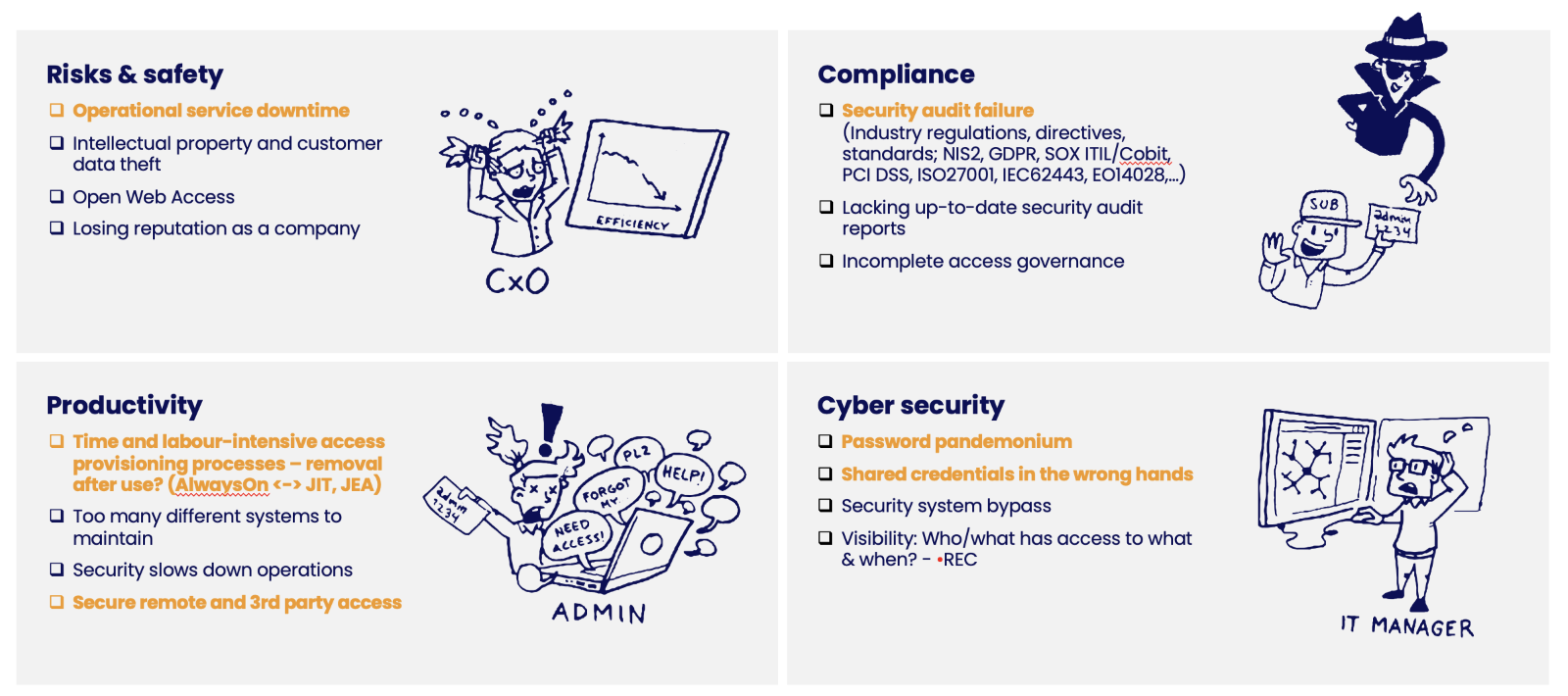
Major risks of access management in OT systems
Managing access to OT (Operational Technology) systems is critical for maintaining the security and integrity of industrial processes. Here are listed the major risks associated with OT security access management:
OT Security de-facto risks:
- Physical Security: Inadequate physical security measures can allow unauthorized individuals physical access to OT systems, enabling them to tamper with or sabotage equipment.
- Legacy Systems: Many OT environments still rely on legacy systems with outdated security measures, making them more vulnerable to attacks.
- Inadequate Monitoring: Lack of real-time monitoring and auditing of access attempts and activities can result in delayed detection of unauthorized or suspicious behaviour.
OT Security technical risks:
- Unauthorized Access: Unauthorized individuals gaining access to OT systems can disrupt operations, steal sensitive information, or even cause physical harm to equipment and personnel.
- Unsecure Remote Access: Remote access to OT systems, if not properly secured, can be exploited by attackers. This is especially relevant with the increasing connectivity of industrial control systems to the internet.
- Weak Authentication: Weak or compromised authentication methods, such as default passwords or easily guessable credentials, can provide an entry point for attackers.
- Lack of Segregation of Duties: Inadequate separation of duties can lead to individuals having excessive privileges, increasing the risk of abuse or errors.
- Failure to Revoke Access: Failure to promptly revoke access when an employee changes roles, leaves the organization, or when access is no longer needed can leave systems vulnerable to unauthorized use.
- Insider Threats: Employees or contractors with legitimate access to OT systems may abuse their privileges intentionally or unintentionally, either through negligence or malicious intent.
- Supply Chain Risks: Third-party vendors or suppliers with access to OT systems can introduce security vulnerabilities if their own systems are compromised.
IT-OT Common language via Purdue model
Traditionally OT networks have adopted various Models, Architectures and Systems to secure the OT Infrastructure. An example is the Purdue Model for Control Hierarchy.
The Purdue Enterprise Reference Architecture (PERA), often referred to as the Purdue Model, is a hierarchical framework used to structure industrial control systems (ICS) and networks in manufacturing and critical infrastructure environments.
Developed in the 1990s at Purdue University, this model categorizes industrial systems and networks into distinct layers, from physical equipment on the factory floor to enterprise-level information systems. The Purdue Model provides guidelines to separate systems by function and security zone, which is essential for cybersecurity and operational efficiency.
The Purdue Model for Control Hierarchy is a common and well understood Model in the Manufacturing Industry that provides a Blueprint to segments Devices and Equipment into hierarchical functions.
What are the 5 Purdue model levels?
- Level 5 (corporate network) covers the enterprise IT systems that cover connections with the public internet.
- Level 4 (IT systems) consists of IT networks such as enterprise resource planning (ERP) systems, database servers, application servers, and file servers that enable the enterprise to drive business logistics systems.
- Level 3 (manufacturing execution systems) is where the production workflow is managed on the manufacturing floor using customized systems for various functions, including batch management, record data, and manage operations and plant performance. These systems also put together lower-level data that gets pushed up to the higher-level business systems.
- Level 2 (control systems) houses the ICS including HMI and SCADA systems in order to supervise, monitor, and control physical processes.
- Level 1 (basic control) hosts the control devices such as sensors, pumps, and actuators, which sense and manipulate the physical processes in order to drive efficiencies.
- Level 0 (physical process) is where the physical equipment that defines the actual physical processes is found.
The Purdue model is shown in the following picture.

What is the Remote Access flow recommended for IT-OT Convergence in the Purdue model?
As part of IT-OT convergence activities we recommend the following way for remote access:
- Remote access GW is placed to a DMZ in level 3.
- Remote access clients are authenticated against enterprise AD and they get an IP address from DMZ.
- Clients use RDP/VNC/Citrix to connect to jump hosts in level 3. These connections are authenticated against a separate ICS AD.
- Jump hosts are dedicated per role / task that needs to be performed. They are hardened and have all the necessary tooling installed.
- Bring your own tools / bring your own data is not allowed.
The following pictures show how remote access activities are represented in the Purdue model.

How to consider NIS2, IEC 62443 when dealing with Access Controls?

How can SSH help with the Access Management of IT-OT Converged systems?
As IT and OT are converging, it's time to bridge the security/safety gap between IT and OT to protect critical infrastructures, energy grids, production sites, power plants, cyber-physical systems (CPS), or machines.

We offer, via our PrivX OT tool, a definitive and cost-effective solution portfolio to enable plant-wide security and enable digital services adoption, from remote assistance to data collection
PrivX OT by SSH Communications Security is a secure access management solution for industrial automation and manufacturing businesses that require access management at scale helping to:
- Integrate with IT/OT systems and provide secure access to modern as well as legacy ICS targets in hybrid environments to allow for local and remote troubleshooting and data collection.
- Support, as a software-based solution, least-privilege and just-enough-access models that are not available with traditionally used VPNs and firewalls.
- Grant just-in-time Zero Trust access to industrial targets, mitigating the risk of shared or leave-behind credentials.
- From industrial control systems to programmable logic controllers, SCADA, and plenty of other OT types, PrivX offers comprehensive cybersecurity for your IT OT landscape.
PrivX OT major benefits include:
- Easy-to-use, secure remote access and maintenance: PrivX OT is fast to deploy with no software agents on the client or the server and no complex configurations. It allows you to enhance productivity thanks to single-sing-on (SSO) and always verified access.
- Acces your IT/OT as one: Support your various IT as well as OT protocols (SSH,RDP,HTTPS, VNC, TCP/IP) allows you to combine your IT/OT data. You can easily analyze your process and product data and increase operational efficiency without the fear of data compromise.
- Stay in control with centralised access management: PrivX OT allows you to manage all your targets under a single pane of glass with full visibility into roles, sessions, sites and targets.
- Comply with regulations: PrivX OT Edition help you stay compliant with strict regulations applicable to remote access, automation, control system applications, and network and information systems: ISA/IEC 62443, ISO 27001, NIS/NIS 2.0, and NIST.
PrivX OT high level solution overview is shown in the following picture.

Massimo Nardone
Massimo Nardone serves as the Vice President of Operational Technology (OT) Security at SSH Communications Security Plc. He collected more than 28 years of working experience in the IT/OT/IoT cybersecurity environments in multiple cybersecurity leadership positions like CISO, Lead Architect, OT/IoT/IIoT Global...
