Nowadays, advances in quantum computing are moving at a neck-breaking pace. Giants in the field have been faithfully executing roadmaps and delivering on milestones laid out several years ago. And while it is hard to predict when the advances will reach their breaking point, the threat to classical, public key cryptography is getting closer.
In this article, we discuss the practical threats to SSH encryption posed by viable quantum computers, prioritization, and pointers on embarking on a crypto-agility journey.
Contents
Public Key Cryptography in Danger of the Quantum Threat
Secrecy of Communications in the Post-Quantum Cryptography World
Granting Access with SSH Keys in the Post-Quantum Cryptography World
The Path to Crypto-Agility
Start Your Journey to Quantum-Agility with SSH
Public Key Cryptography in Danger of the Quantum Threat
As quantum computers advance on the path to becoming a notable threat, the question is: When is the time to act, and how to prioritize your actions?
The short answer is: It depends on the use case.
The longer answer is: Public key cryptography is in danger. You should concentrate your efforts on protecting your communications, data, and access to them, and you should embark on the journey toward quantum safety as soon as possible.
In the context of encryption used in SSH applications, public key cryptography performs two important functions:
- Key exchange, which facilitates the negotiation of session keys for the ultimate purpose of establishing a secure end-to-end encrypted communication tunnel. In other words, it’s the bedrock of security provided by SSH, the promise of secrecy of communication.
- Digital signatures, which provide a method for verifying the authenticity of digital messages, documents, or identities. In the context of the SSH protocol, digital signatures are used as part of user and host authentication via the utilization of SSH keys or certificates. Specifically, digital signatures are used to sign session-specific challenges that prove ownership of a host key or a private key. The keys belong to real users or machine-to-machine identities that grant access as well as path validation of certificates, which have been signed by a Certification Authority.
Secrecy of Communications in the Post-Quantum Cryptography World
Key exchange (KEX) algorithms within SSH should be of high priority on your journey toward quantum safety. Especially for systems protecting long-term secrets, such as customer data and other network protocols (like IPsec), since the key exchange is responsible for establishing the secure channel.
The risk
With sufficiently advanced quantum computers, compromising end-to-end encryption would be trivial and potentially possible in real time. This effectively allows third parties to eavesdrop on the communication.
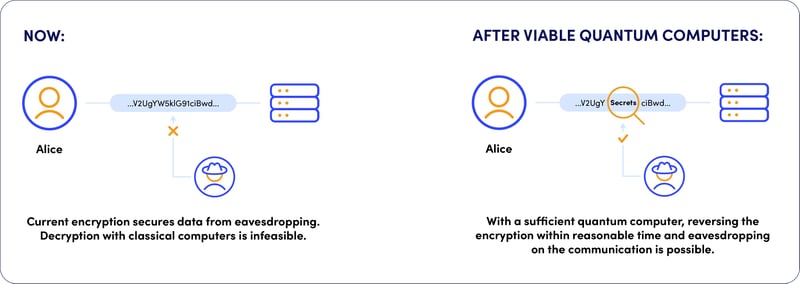
The urgency
While this attack vector requires the availability of quantum computers, current encrypted sessions can be recorded and decrypted later, once powerful enough quantum computers are available.
Migrating to Quantum-Safe Key exchange algorithms is the highest priority mitigation action that should be done as soon as possible.
Granting Access with SSH Keys in the Post-Quantum Cryptography World
The second important task of public key cryptography within SSH is its role in granting access to user and machine identities through the utilization of SSH keys.
SSH servers verify the entity requesting access via a series of cryptographic functions, ultimately granting access only to the bearer of the correct private key.
Private keys, like passwords, are access credentials. For that reason, they are a prime target for collection by malicious actors as SSH keys are a common way to provide lateral movement within the server estate and privilege elevation.
The risk
With sufficiently advanced quantum computers, malicious actors don’t need to go through the hassle of harvesting private keys since they will be able to derive them from their public counterparts - a feat computationally out of reach for classical computers.
Like this, impersonating legitimate holders of private keys will become trivial.
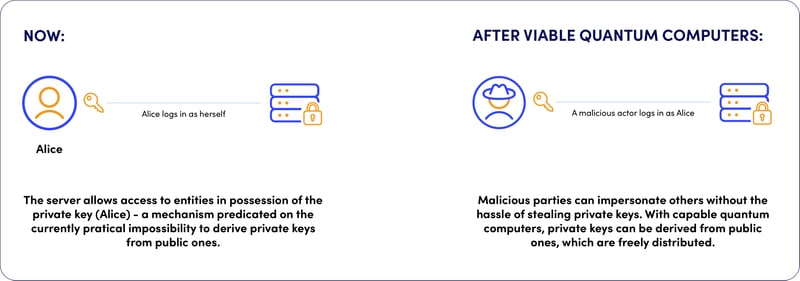
The urgency
Replacing current SSH keys is predicated on the development and standardization of quantum-safe signature key algorithm(s). Efforts are ongoing and the industry expects to see emerging proposals in the near future.
The Path to Crypto-Agility
Considering the current advances and availability of quantum-safe (QS) algorithms, the path forward calls for a multi-staged approach including evaluation, adoption, and ultimately migration away from classical towards quantum-safe encryption.
- The evaluation stage means the assessment of the current state of the SSH environment. This helps report progress and reveal areas where quantum-safe algorithms are available but not in use.
- The adoption stage is the transitionary period, during which QS encryption usage is implemented alongside classical algorithms. This ensures that SSH connectivity can still be allowed for applications that do not yet support QS algorithms.
- Finally, the migration stage is a complete transition away from classical encryption towards QS algorithms. This ensures the preservation of the secrecy and integrity of communication in a post-quantum world.
Start Your Journey to Quantum-Agility with SSH
SSH Communications Security provides a quantum security portfolio that is uniquely positioned to help in your journey toward quantum-agility.
As the latest addition to SSH's portfolio of quantum-safe products, Universal SSH Key Manager (UKM) can evaluate and produce reports on the adoption level of Quantum-Safe Key Exchange Algorithms available presently as well as alert on classical algorithms known to be vulnerable to classical computing and enforce the usage of the quantum-safe KEX algorithms.
UKM can also monitor for unwanted usage of obsolete encryption and alert security professionals to take action. All while keeping the infrastructure compliant with contemporary encryption standards.
In the future, when QS signature algorithms gain acceptance and have been standardized, UKM will automatically replace SSH keys using classical algorithms with QS ones. In the meanwhile, UKM can be used to replace SSH keys considered weak by current standards with ones that are expected to withstand longer than the weaker parameters against the quantum threat.
Marieta Uitto
Marieta Uitto is a product manager currently focusing on driving roadmap and collaboration with customers to successfully solve their challenges. She has spent over 15 years with SSH.com of which more than ten, working in R&D with exceptional teams to deliver industry leading products. PAM solutions, Key Management...
