SSH Overall Leader in KuppingerCole’s Dynamic Access Management Report
KuppingerCole Analysts just published their Dynamic Resource Entitlement & Access Management (DREAM) classification for access management and entitlement platforms that can best operate in dynamic computing environments.
This report is first of its kind for the market research company, and it puts special emphasis on platforms that “must operate at the speed of the cloud and grant access based on tasks, toolchains, and workloads rather than roles – or only permission access to static resources such as servers or vaults”, as is stated in the report.
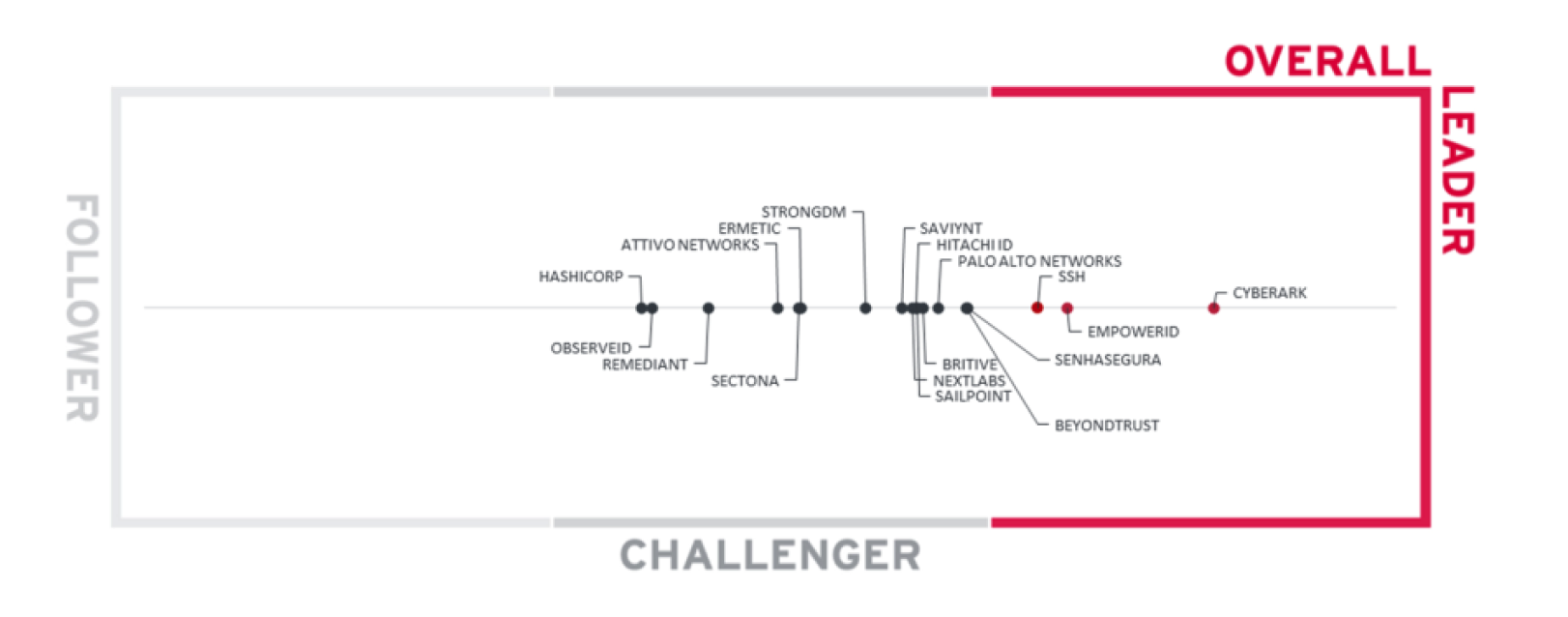
We at SSH are happy to announce that we are ranked as an 'Overall leader in this document. We were leaders in the following categories:
- Market Leaders
- Market Champions
- Product Leaders
- Innovation Leaders
Download the report here for free, courtesy of SSH!
Contents
What Is Dream?
Vaulting, Standing Privileges, and Cloud Workloads Are Not the Optimal Combination
Just-in-Time Zero Trust with Zero Touch Is Gaining Recognition
Passwordless is great - but what about encryption keys?
JIT Zero Trust Access Management for Keys and Passwords
What Is DREAM?
In essence, this is a new category for access management solutions, since the platforms covered include those traditionally categorized as CIEM (Cloud Infrastructure Entitlement Management), Identity and Access Management (IAM) and Privileged Access Management (PAM).
Since the operating environment is changing, it’s a great initiative from KuppingerCole to challenge the status quo of the access and entitlements management landscape. Maybe multi-cloud and hybrid cloud environments need a new classification of tools that are better equipped to meet the need for speed, agility, and effectiveness prevalent in cloud-driven environments.
Some key characteristics for a solution to be included in the report include:
- Native Support for multi-cloud services like AWS, GCP, Azure
- Agentless deployment
- Just in Time (JIT) access for users, machines, and service accounts
- Multi-cloud discovery tools
- Centralized and easy to read dashboarding
- Alerting and reporting mechanisms
- Enforcement of Least Privilege
- Connectors to both cloud services and on-premises applications
- Entitlement Management, including Role Management
- Native Orchestration Tool support e.g., Kubernetes
- Workflow and task-based authentication
- Session Recording and Monitoring
Vaulting, Standing Privileges, and Cloud Workloads Are Not the Optimal Combination
"The CIEM and DREAM sector is impacting on classical PAM; its vaults and standing privilege architectures are increasingly too slow for dynamic cloud workloads."
- Paul Fisher, Kuppingercole in DREAM
Vaulting, storing, and rotating credentials has been the bread and butter for PAM solutions for quite some time. This method is still necessary in many (legacy) instances but sticking only to this method has not been necessary for many years. And as stated by KuppingerCole, it’s also too slow.
Advanced Zero Trust means Zero Touch, Just-in-Time and Passwordless Access
Many incumbent PAM vendors have tried to improve their credential management game by creating one-time passwords (OTP). The password is stored in a vault, issued to the user at the time of making the connection, a temporary account is created at the target host and the connection is made. Then the account is deleted, and the password rotated. Rinse and repeat.
It might sound good in theory, but this method is still using standing privileges that are just rotated more often than before. In reality, it means that your environment is never stable, since temporary passwords and accounts are being created and deleted all the time.
But the times they are a-changing. We at SSH introduced our short-lived certificate-based approach to privileged access management already in 2017. It introduced three key elements:
- Zero Trust
- Zero Touch
- Just-in-Time
In this model, access is granted just-in-time (JIT) for authentication, and all the secrets needed to establish the privileged connection are baked into an ephemeral certificate that automatically expires within minutes afterwards. It simply leaves no passwords or encryption keys behind to be managed. The privileged user never sees or handles those secrets either, aligning with the true meaning of the word Zero Trust.
What’s more, this model keeps your environment immutable. No temporary passwords, accounts, or any configuration changes. It’s all very lean and clean, making it Zero Touch.
This is what we mean with advanced Zero Trust:
- Minimize the configuration changes to your environment to support immutable infrastructures
- Eliminate all the unnecessary touch points
- Radically reduce the need for processes that you need to monitor and invest hardware in
All in all, it’s economical, scalable, and more secure than the traditional models.
Just-in-Time Zero Trust with Zero Touch Is Gaining Recognition
Our ‘JIT ZT’ approach has been gaining recognition over the years. KuppingerCole recognized its merits already in 2020 in the Leadership Compass: Privileged Access Management by ranking our product as a leader in multiple categories. In 2021, in the Leadership Compass: Privileged Access Management for DevOps report, our solution was highlighted as an ideal solution for DevOps. Now, in the DREAM report, our approach is validated to be one of the best for the future-driven organizations.
Also, Gartner has taken note of the changing landscape. In their Remove Standing Privileges Through a Just-in-Time PAM Approach, Gartner recognized our approach as rather unique on the market.
"Another vendor, SSH.COM, is introducing an approach to JIT access with its 'lean' PAM approach. This approach uses 'ephemeral' access, granting one-time, short-lived certificates for elevating user access."
- Gartner in Remove Standing Privileges Through a Just-in-Time PAM Approach
More information about the Gartner document here.
This year, Gartner has put passwordless authentication in the spotlight in the The Gartner Emerging Technologies and Trends Impact Radar.
The passwordless trend is strong overall now. Microsoft, Apple, and Google are all recommending passwordless authentication methods over password rotation, management, or vaulting.
Our solution has been growing by 200% on the market for the past few years, so there is real traction here as well.
This is no wonder. The problems and challenges related to password management are well-known. You can learn more about them in our blog post about password management and rotation here.
Passwordless simply wipes out many problems that purely management-based solutions create.
Passwordless is great - but what about encryption keys?
One topic that is often ignored even by such established and esteemed players like KuppingerCole and Gartner is encryption key management. We often find that in customer environments, SSH keys outnumber passwords by the ratio of 10 to 1. Just like passwords, SSH keys open door to critical data, infrastructure, or systems, like credit card databases, company’s IT network, or industrial control systems (ICS).
Therefore, we propose passwords and keys should be managed together under a single pane of glass. The idea is to find your passwords and keys and then get rid of as many as possible with a sensible migration plan. Pure cloud environments are most likely to be rare. Hybrid cloud environments with a mix of on-premises and multi-cloud services are most likely to be the favored option for many companies. In the similar fashion, secrets management is a hybrid of passwordless and keyless environments supported by managing credentials with vaulting and rotation.
JIT Zero Trust Access Management for Keys and Passwords
We at SSH recommend you migrate to a passwordless and keyless environment at your own pace. With non-intrusive deployment, SSH enables you to begin going credential-less while continuing to manage existing passwords and keys (by vaulting and rotating them) in the meantime. This contributes to more secure, organized, and manageable credential management processes.
Learn more about our unique just-in-time zero trust access management here.
PS. Don’t forget to download the KuppingerCole report here.
Jani Virkkula
Currently employed by SSH.COM as Product Marketing Manager, Jani is a mixed-marketing artist with a strong background in operator and cybersecurity businesses. His career path of translator->-tech writer -> marketer allows him to draw inspiration from different sources and gives him a unique perspective on all types...

