Why the Manufacturing Industry Should Get Serious About Zero Trust and Just-in-time Access
Let’s face it – manufacturers, critical infrastructure (CI) operators, energy businesses and utility companies are experiencing an unprecedented volume of threats in the cyber domain. In addition to the proliferation of malware attacks and digital theft attempts, industrial operators need to deal with increasing pressure on operating costs and sustainability, regulatory scrutiny, and a heightened public awareness of cybersecurity.
It’s no wonder that more and more companies have realized the importance of secure remote access to their sites. After all, they are being accessed by internal admins, 3rd party technicians and a host of other experts in the supply chain. Existing security controls might include traditional solutions like VPNs and firewalls, but do they really offer enough functionality, granularity or scalability to meet industrial-scale needs?
Dedicated solutions like Privileged Access Management (PAM) solutions help companies in both traditional IT and Operational Technology (OT) domains protect their most valuable assets. However, not all PAMs are created equal, and not every PAM solution can meet the needs of real-world OT environments. Key PAM requirements for OT-poof secure remote access include:
- Clear and easy-to-use structure for managing users, targets, and credentials
- Essential security features missing from legacy OT access solutions, such as multi-factor authentication (MFA), role-based access control (RBAC), and audit trails
- Ability to synchronize identities from multiple directories, including AD, LDAP, and OpenID
- Productivity enhancement through single-sign-on (SSO) and HTML5 ‘thin-client’ user interface
- A high-level of automation for minimized need for manual configurations or maintenance
Here’s a comprehensive look into why a lean, modern PAM that supports Zero Trust is the ideal fit for industrial OT access management.
1) Get control of your OT targets, users, and credentials
Digitalization, automation, and increasing reliance on real-time data analysis have had a huge impact on the connectivity requirements for industrial automation and control systems (IACS). No longer disconnected from the outside world, such OT systems should be accessible remotely by administrators, engineers, and maintenance technicians alike.
The sheer number of target devices, accounts, and user identities can quickly reach tens of thousands, as sensors, industrial applications, robotics, medical devices and software-defined production processes are predminantly data-driven and require updates and maintenance.
This easily turns into a mess, where access rights to systems cannot be properly controlled, or the required digital keys (like perhaps the most prevalent ones in Operational Technology, SSH Keys) are distributed quite carelessly.
To make matters worse, OT systems have not typically been designed with sophisticated access management in mind, and integration to enterprise-wide identity and access management (IAM) systems can be challenging.
What if your access management to all your OT targets could be handled within one pane of glass, regardless of the number or location of users, hosts, and physical sites?
2) ICS/SCADA systems are being targeted as OT breaches are trending up
Norsk Hydro and Maersk are perhaps the best-known breaches in the world of OT. In both cases, the companies’ critical production IT systems came to a grinding halt, and losses were measured in the dozens of millions of euros.
In 2020, the semiconductor maker Tower had to discontinue its chip production due a ransomware attack, resulting in multiple lost weeks of full activity levels. Just recently, a hacker breached a Florida water treatment plant and added lye to the water supply. Also, a fuel pipeline run by Colonial Pipeline was forced to shut down because of a breach,
In addition to monetary cost and the risk of theft of intellectual property and business disruptions, hackers could, in the worst case, alter the physical output of the manufacturing process, impacting the safety or functionality of products on the market. Or as in the water treatment breach, put lives at risk.
Unfortunately, operational technology continues to represent a large attack surface for cyber criminals, not least because OT systems have traditionally focused on efficiency and safety, instead of IT security.
This is no wonder: IT/OT convergence is a paradigm shift to the OT industry, and in-house teams understandably lack the required expertise. They also often find the change of pace overwhelming and have challenges staying up to speed with current security tactics and measures.
While converged IT/OT systems become more prevalent, one compromised subsystem can bring down an entire global manufacturing chain, making recovery time-consuming and costly. Therefore, manufacturing industries are among the prime targets for hackers.
Traditionally, OT security has been implemented on a basic level with security zones as described by the Purdue model. While the hierarchical approach provides a security foundation for OT systems architecture, it fails to take into account the connectivity requirements of modern industrial internet of things (IIoT) systems and remote access.
Although demilitarized zones (DMZ) and firewall-VPN based controls are a good start, they lack the ability to identify, authenticate, and authorize individual users and provide the granularity needed to defend against sophisticated infiltration attempts.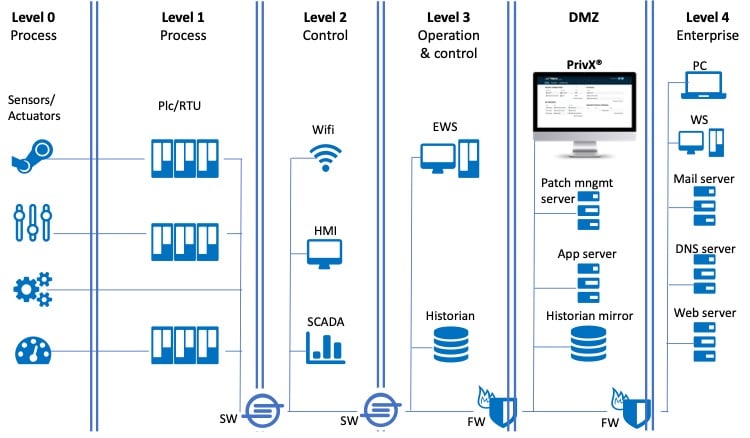
Protecting Supervisory control and data acquisition (SCADA), programmable logic controllers (PLC), the human-machine interface (HMI) and remote terminal units (RTU) takes a bit more sophistication in IT/OT convergence.
Here are some examples of how a modern PAM solution can safeguard manufacturing companies against intruders:
- Strong authentication: all users will be authenticated by MFA if required.
- Zero Trust: access privileges are granted and accepted in real time and just-in-time fashion, based on the user’s authorization level.
- Logging of access events: All connections are logged, actions can be traced back to individuals, and user identities are stored for auditing purposes. Security Information and Event Management (SIEM) integration can be used to create alarms for dubious access attempts.
3) Enable secure remote work, 3rd party, partner and global vendor access
Industrial processes depend on an increasingly complex network of machines, automation and control systems, metrology equipment, sensors, and analytics solutions. The administration and maintenance of this system and its parts is increasingly done remotely, either from within the enterprise network or over the public internet. 3rd party specialists might be responsible for monitoring systems at dozens of sites, on multiple continents and time zones.
A modern PAM solution can provide seamless and secure access to OT systems using a browser-based, agentless connection. From PrivX’s HTML5 web interface, partners can simply select the targets they are allowed to access by pointing and clicking, establishing encrypted connections instantaneously, without the need to enter usernames or passwords - and without being able to see or share them.
Supported protocols include SSH, RDP, and HTTPS, VNC and other protocols though connected application containers or gateways - thus enabling access to virtually all commonly used OT platforms.
4) Vault standing privileges, privileged passwords and shared secrets - or get rid of them!
Standing privileges, such as static target host usernames and passwords, are a permanent addition to the attack surface for nefarious actors. Privileged credentials are a desirable target for hackers, since they are generally trusted to be in control of a limited group of power users. Outsourcing has a lot of business benefits but it also means that you have to grant powerful access to people working outside your company.
Now if you combine permanent privileged accounts given to 3rd parties and hackers who actively harvest permanent credentials, the potential attack surface increases exponentially. To make matters worse, OT systems often have limited support for modern identity or account management solutions, and 3rd party users often end up sharing user credentials, e.g., passwords, and storing them in potentially unsafe locations.
Once out in the open, the credentials can provide unlimited access to critical resources for as long as the accounts exist unchanged on target systems. Unfortunately, account management is often left to unreliable, haphazard manual processes in OT environments.
Our PrivX offers two different ways to guard your secrets. The first option is very traditional: secrets stored to a vault for minimal exposure to attackers, ex-employees, or past contractors.
The second is a more modern, cloud-proof approach that we always recommend: PrivX gets rid of having to manage passwords and standing privileges and replaces them with Zero Trust access where credentials are generated on the fly and then expire automatically after the connection is established. There simply are no leave-behind credentials or digital keys that need to be vaulted or could be stolen. Your privileged users don’t see or handle any secrets at all.
Why these two different options, then? Many customers find that they need to vault passwords and digital keys just to get them under control or that some environments are not technologically viable for passwordless access. They can then migrate to passwordless authentication methods when those environments and applications are modernized.
This approach not only aligns with the Zero Trust framework but also adheres to Gartner's Zero Standing Privileges model.
5) Give Just Enough Access (JEA), Just-In-Time (JIT), using Role-Based Access Control (RBAC)
Some end users such as site administrators or systems engineers need to access multiple OT systems frequently. Others may only connect to specific targets during scheduled maintenance events, while some may be called upon as needed to perform one-off trouble-shooting jobs or software updates.
OT access management should cater to the needs of all these groups by providing the required level of privileged access – Just Enough Access (JEA), or ‘least privilege’ – to the specific assets needed to get the job done. What is more, access privileges should adapt to changes in the organization and business needs, staying in sync with joiners, movers, and leavers.
Role-based access control (RBAC) is a modern access control mechanism defined around roles and privileges. Simply put, users are first authenticated, and then assigned to roles. Access authorization to OT targets is granted based on the role as defined by rules such as Lightweight Directory Access Protocol (LDAP) or Active Directory (AD) group membership. Roles can also be granted upon request, e.g., to give a technician limited-duration access to an asset in need of repair.
The RBAC approach separates the user identities and authentication from the access credentials and adds security by removing the need to distribute credentials to individual users or end points. By adjusting role memberships, access to OT targets can be granted, elevated or revoked in real time, fulfilling the requirement for Just-In-Time (JIT) access.
The result is that you get appropriate level of access limited by the role for internal and external workforce alike.
6) Get compliant with NIST, NIS (2.0), ISA and IEC 62443
With the critical nature of many industrial supply chains, it’s no wonder that government agencies, public regulating bodies and standardization institutions have long since raised OT cybersecurity as one key area of interest.
For example, the NIST Cybersecurity Framework and International Society of Automation (ISA) makes several recommendations for managing user identities and credentials, authorized devices, remote access, and access privileges.
The IEC/ISA 62443 series of standard provides a further framework to mitigate security risks of IACS, making up a significant part of what is current understood to be a ‘best practice’ for OT security. A future-proof, PAM system is an essential tool for ensuring compliance with these requirements.
The EU Cybersecurity Act, and the 2016 Directive on Security of Network and Information Systems (NIS) impose additional requirements for utilities providers, financial institutions, information infrastructure and healthcare operators in the EU.
The upcoming new revision NIS 2.0 will expand the requirements to a number of ‘important’ entities. This includes medium-sized and large companies and select smaller entities in several manufacturing sectors, including chemicals production and food processing.
As a result, tens of thousands of organizations will need to take a fresh look at how to enhance the security and efficiency of their OT infrastructure. In most cases, a PAM deployment will be a critical element in ensuring regulatory compliance.
7) Secure your OT legacy systems
Most OT systems in current use were not designed with remote access or cybersecurity in mind. Moreover, the multitude of connection protocols and lack of account management features in legacy systems have pushed OT managers to opt for a variety of jump host, applications servers, and virtual desktop solutions to provide the access needed.
Such workarounds are rarely easy to scale and maintain, and lack compatibility with enterprise identity management solutions, single sign-on, or MFA. The end result can be cumbersome to use, difficult to manage, and – worse yet – fails to meet modern security requirements.
When a PAM solution such as PrivX is tailored for OT remote access, top-notch security, ease-of use, automation, and expandability are built right in from the very start. User identities and authentication can be federated from an on-premises LDAP, AD, or cloud-based IAM, event logs can be exported to SIEM or Security Operations Center (SOC), and any OT target in the enterprise can be accessed securely with just a few clicks. No end point clients, no jump hosts, no passwords, no hassle.
Get started on securing your industrial automation and assets today. Learn the basics in two minutes in this overview video of PrivX.
If you want to learn more about how just-in-time access with zero standing privileges is ideal for OT, learn more about the topic below.

Miikka Sainio
Miikka guides the software architecture and development at SSH. He has over 20 years of experience in IT industry, building teams and developing products in startups and large enterprises.
