SalaX Secure Mail
What our customers say about SalaX Secure Mail:
Really good product for everyone who cares about their email security.
"The product works and if not, the support will help quickly."
- IT associate, construction industry
The product is working as it should.
"Outstanding help, service is good/helpful and product is working as it should."
- IT associate, insurance (except health) industry
Full-on email security with SalaX Secure Mail
Access verification
Verify all users (senders and recipients alike) with various authentication methods (including strong authentication bank ID, SMS OTP, password). Ensure security with monitoring features, like audit trails and various reporting options.
Robust security
Protect your communications with end-to-end encryption, all the way from sender to recipient. Secure Mail supports various email security protocols (DMARC, DKIM, SPF) as well as S/MIME-based encryption.
Full control over your data
You are in control of your data - flexible deployment is possible in the cloud or on-premises. Secure Mail also offers multiple configuration options (APIs, web interfaces).
Quantum-safe
Secure Mail utilises quantum-safe encryption to protect your data from future threats.
Inbound Email
Unlike competitors focused solely on outbound communication, Secure Mail supports inbound email services. Businesses can securely receive inquiries from external users directly through their websites, expanding secure communication capabilities.
User-friendly experience
Secure Mail interoperates with any email system without changes to the user experience. No extensive training for users, no end-user accounts needed.
A browser-based interface makes it easy for third parties to start encrypted communication with your business.
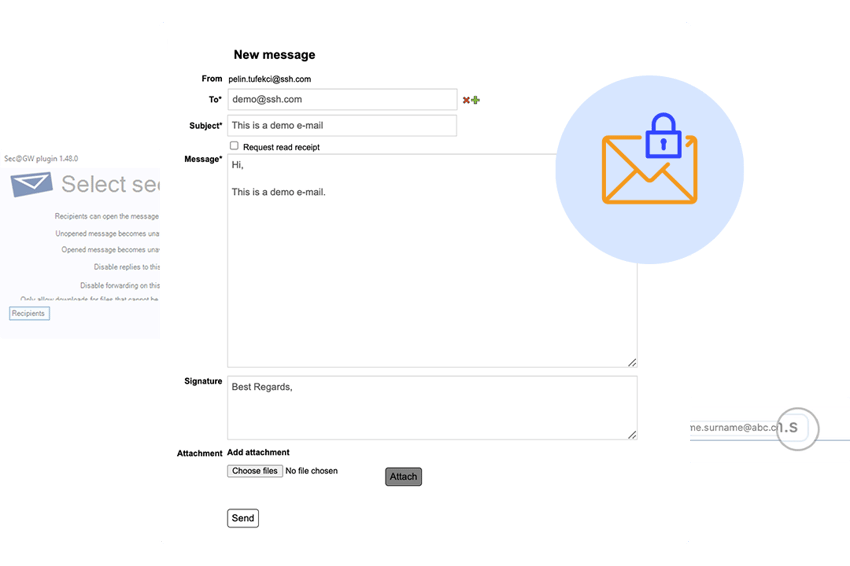
How does SalaX Secure Mail work?
Sending a secure email via web client:

Step 1: Log in using your preferred method, e.g. email and password.
Step 2: Create a new message by filling in the recipient's email address, subject, and email body. You can attach files up to 1GB.
Step 3: Adjust security settings such as your preferred authentication method for the recipient (password, email OTP, etc.).
Step 4: Send the secure email.
Sending a secure email via an email client (e.g. Outlook):

Step 1: Connect your email client with Secure Mail and create a new message as usual.
Step 2: Add ".s" to the recipient's email address.
Step 3: Send the secure email.
Receiving a secure email:

Step 1: Open a notification email and click the "Access the message" button.
Step 2: Authenticate using the sender-selected method.
Step 3: View the secure email. Based on sender-selected security settings, you may reply, forward, save, or delete the message.
How to use inbound email:
Step 1: Configure Secure Mail
Set up inbound messages and choose sender authentication (email, SMS/SSN, or whitelist) in your admin panel.
Step 2: Add Secure Mail URL
Integrate the provided URL onto your website for easy access.
Step 3: Start Receiving Messages
Customers/patient authenticate and send secure messages through the URL.
Sending unencrypted emails is like sending
confidential information on a postcard
- Email is still the most commonly used tool for business communications because of its ease of use and accessibility, regardless of the security limitations of the Simple Mail Transfer Protocol (SMTP) protocol - the standard communication protocol for electronic mail transmission.
- Many webmail solutions have native encryption, but the communications can still become unencrypted on their way to the recipient, making them vulnerable to misuse.
- Traditional Transport Layer Security (TLS) is a cryptographic protocol providing communications security over a computer network. However, it often lacks complete end-to-end encryption.
Let us help you secure your business email! Get in touch >>>

Who benefits from email encryption?
All organizations using email to communicate with their partners, customers, and employees should consider protecting their email traffic, especially if you're sharing business-sensitive information.
Our customers typically protect the following type of highly confidential and sensitive information:
- Financial information
- Recruitment & HR information
- Business development data
- Product development data
- Customer information
- Marketing strategies
- Service requests
- Offers & pricing information
- Confidential project files
- User credentials and/or passwords