
- Solutions
- SOLUTIONS
- PrivX Zero Trust Suite
- SalaX Secure Collaboration
- Strong ID-based access with Entra ID & Zero Trust Suite
- Quantum-Safe Cryptography (QSC)
- Security Risk Assessment, Quantification & Mitigation
- OpenSSH by SSH
- Device trust & access and identity verification
- Identity-based authentication & converged IAM and PAM
- TOPICS
- INDUSTRIES
- SOLUTIONS
- OT Security
- Products
- Services
- Customer cases
- Resources
- Solutions
- SOLUTIONS
- PrivX Zero Trust Suite
- SalaX Secure Collaboration
- Strong ID-based access with Entra ID & Zero Trust Suite
- Quantum-Safe Cryptography (QSC)
- Security Risk Assessment, Quantification & Mitigation
- OpenSSH by SSH
- Device trust & access and identity verification
- Identity-based authentication & converged IAM and PAM
- TOPICS
- INDUSTRIES
- SOLUTIONS
- OT Security
- Products
- Services
- Customer cases
- Resources

for it & ot and msp
PrivX PAM3 - Go beyond traditional PAM.
PrivX is a super-scalable Privileged Access Management (PAM) solution with 30% less TCO for hybrid and multi-cloud environments, including leading SSH key management and any combination of password vaulting, rotation, and passwordless authentication.


versatile privileged access management
What sets PrivX apart from traditional PAMs?

Single pane of glass
Comprehensive IT/OT/MSP access management and use cases. Versatile, audited protocol-level access to the entire infrastructure, including browser isolation.

Zero Standing Privileges
Vault, rotate and manage passwords, keys and other standing secrets – human or machine generated. Migrate to passwordless and keyless authentication for true Zero Trust.

Automated and fast to deploy
Deploy without complex, resource-intensive processes, including agents or changes to production scripts. Ideal for traditional, modern and future environments.

Auto-discovery and ease of use
Auto-scale PAM with minimal resource usage. Auto-discover assets and accounts. Integrate with IAMs, SIEMs and SOCs through APIs. Enjoy top-rated usability.
Customer Cases
PrivX PAM solution in action


E-tailer Manages Privileged Access in a Containerized Environment with 100,000 Servers
Global Microchip Manufacturer Secures 1 Million Machine Connections
PrivX is a highly scalable, versatile and effective PAM platform
"PrivX is an effective tool for managing privileged access to critical systems and environment. It is very scalable tool, yet easy to administer and use."
Vice President of Information Securiy, Global Retail Company
Best Priviledged Access Management Tool In The Market
"This is the best tool that I have ever come across for managing access for different users across tools and servers."
Software engineer, Miscellaneous Industry
Efficient And Secure Remote Connectivity For OT With Core PAM Functionality
"PrivX PAM solution is mainly used for OT access management and PAM usage on this specific area. Product fulfills the need to segregate networks, management and access to different stakeholders into closed networks/systems.”
IT delivery and service owner, manufacturing Industry
PrivX PAM Functionality Matrix
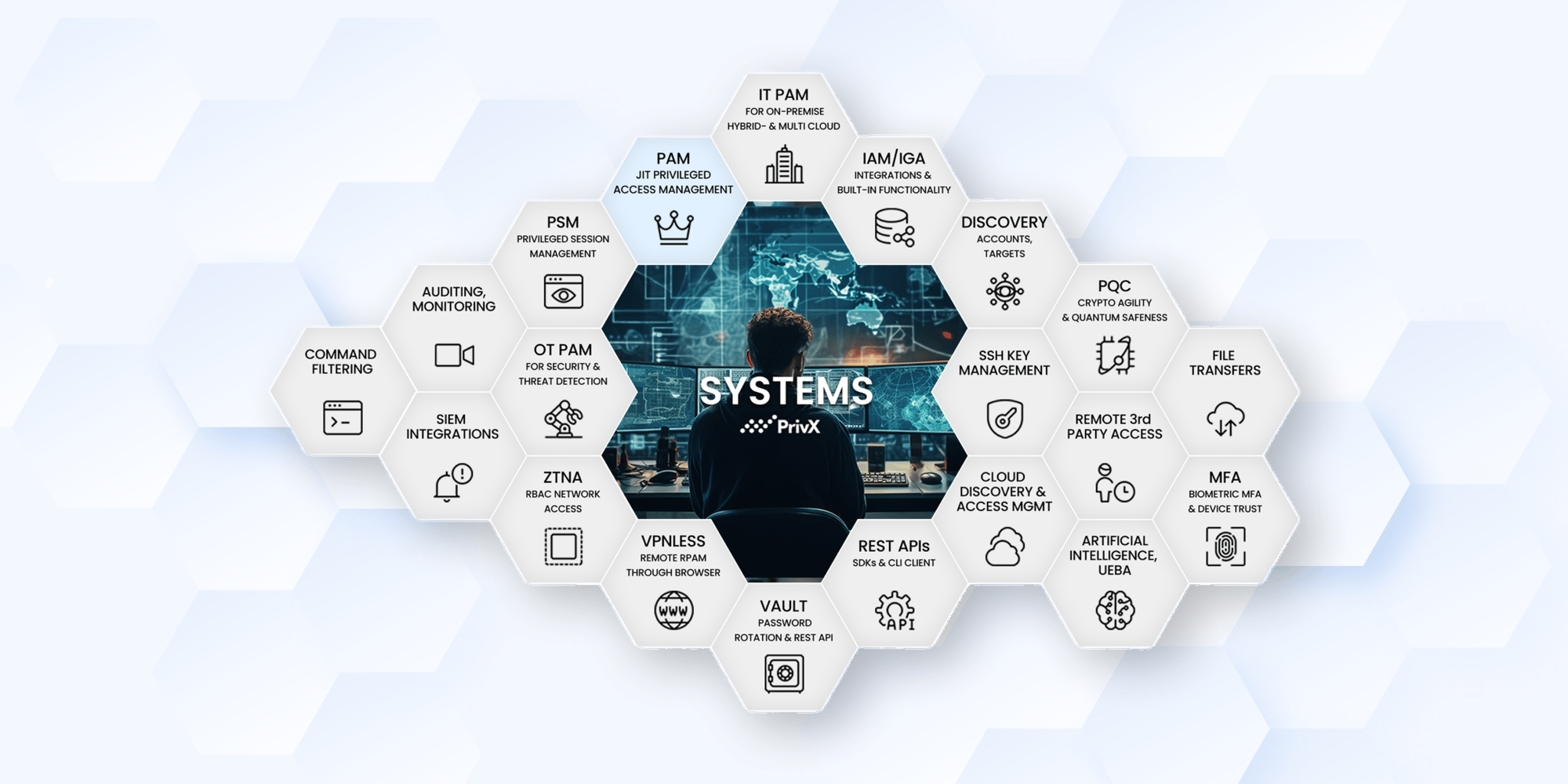
Complete PAM Offering
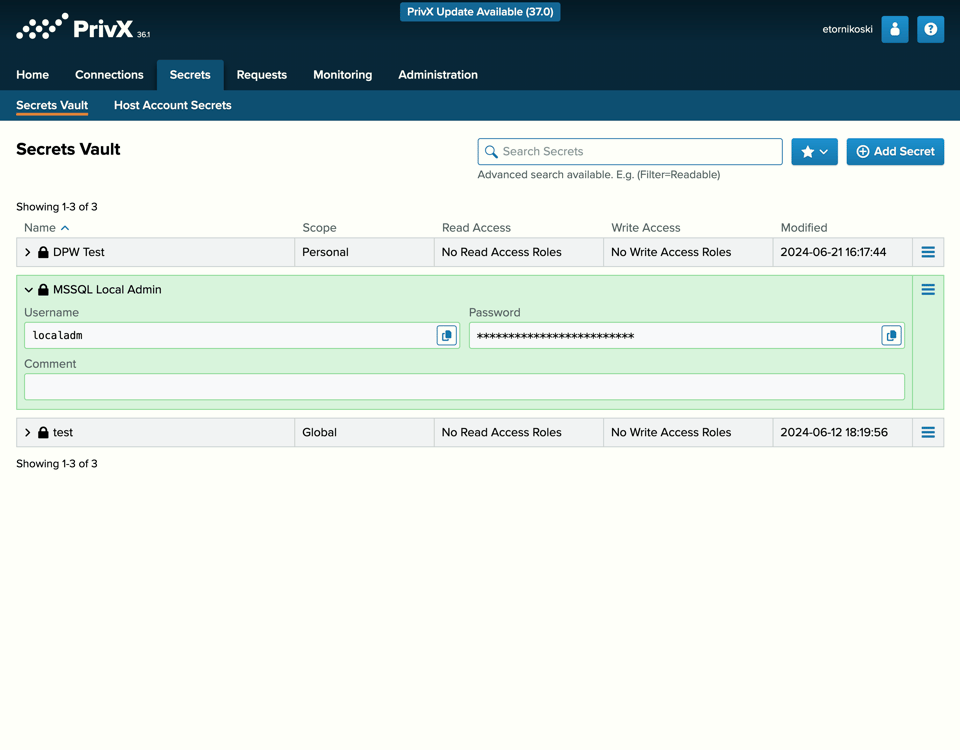
Advanced Privileged Credential Management
-
Supports vaulting, rotation and retrieval of credentials and other secrets.
-
Full life-cycle management of SSH keys.
-
Monitoring and alerting environment of PAM bypass attempts or of policy violations
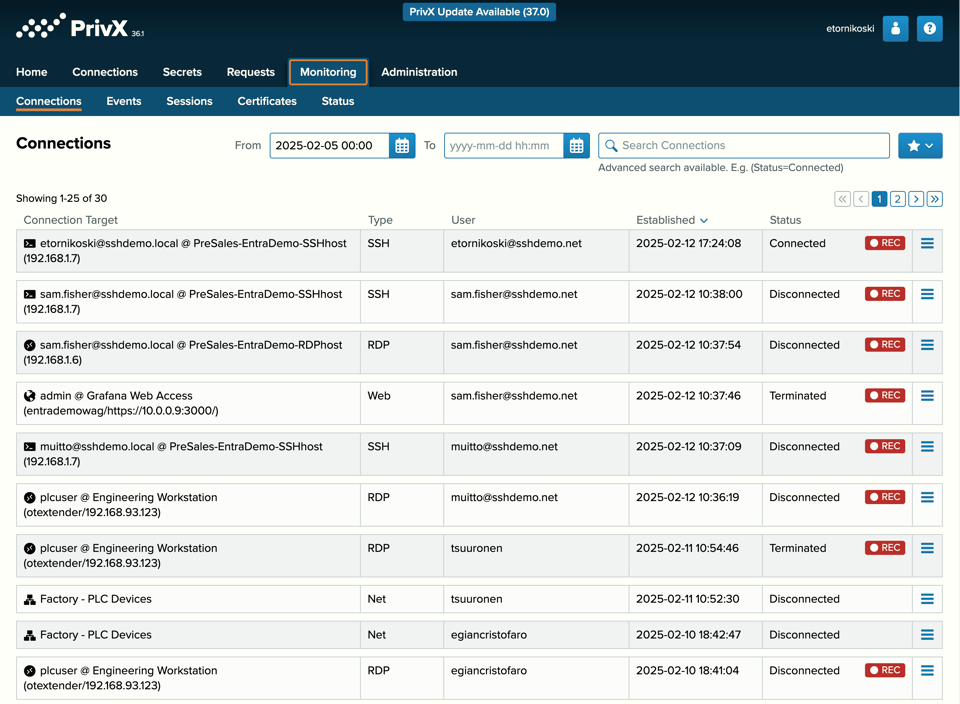
Broad Privileged Session Management
- Generates robust audit trails, session recordings, and allows live monitoring.
- Non-intrusive machine to machine (M2M), application-to-application (A2A) or system-to-system (S2S) connections
- Comprehensive IT/OT/MSP access management with support for SSH/RDP/VNC/HTTP(S)/DB/Modbus/Profinet or browser isolation and Secure Service Edge (SSE)
- Quantum-safe SSH connections
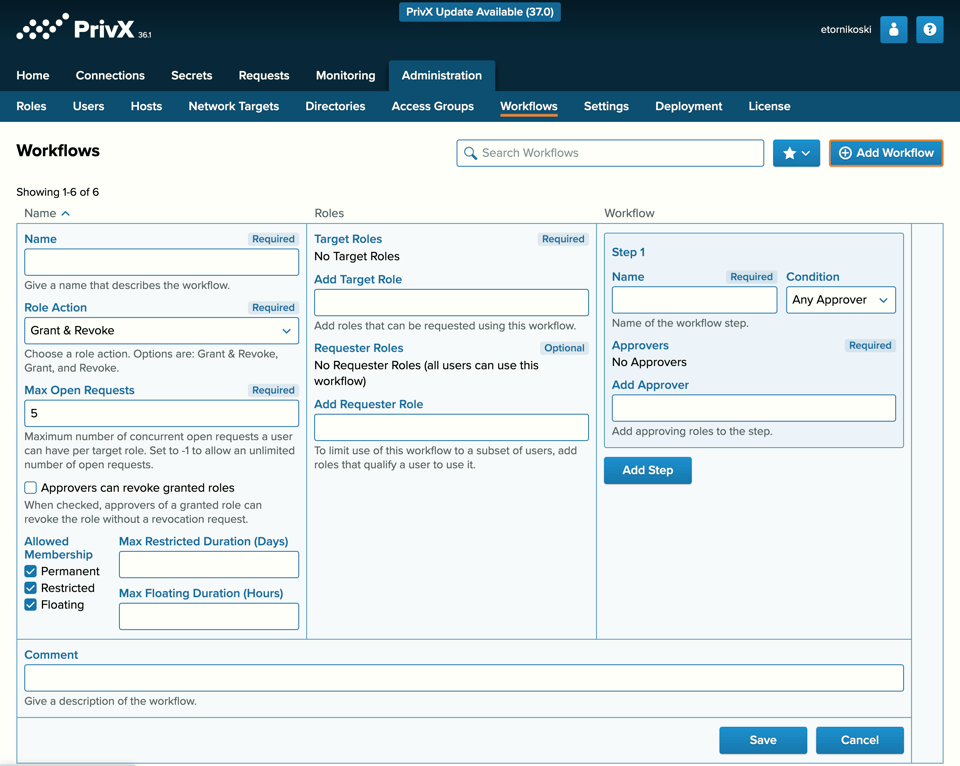
Just-in-time, Zero Trust Access
- Just-in-time (JIT) access with short-lived certificates, allowing migration to passwordless and keyless authentication
- Reduces the risk of unauthorized access, ensures compliance, and streamlines access management.

Identity Management and Governance Integrations
- PrivX integrates with multiple IAM and IGA systems, such as Entra ID, Active Directory (AD), OpenID Connect (OIDC) providers and LDAP
- Role-based access controls (RBAC) ensure that users are granted access based on their roles, providing JIT and just-enough-access (JEA).
- Device Trust ensures the security posture of the client used to access a target and can automatically terminate at-risk connections
Modern and Future-Proof PAM system
Highly automated for great ROI
-
keeps user IDs and access privileges up-to-date automatically
-
maps roles to IDs and security groups and keeps them up-to-date
-
Auto discovers assets (e.g. cloud servers, servers and OT assets)
-
Auto discovers privileged accounts, including cloud user accounts, local accounts, SSH keys)
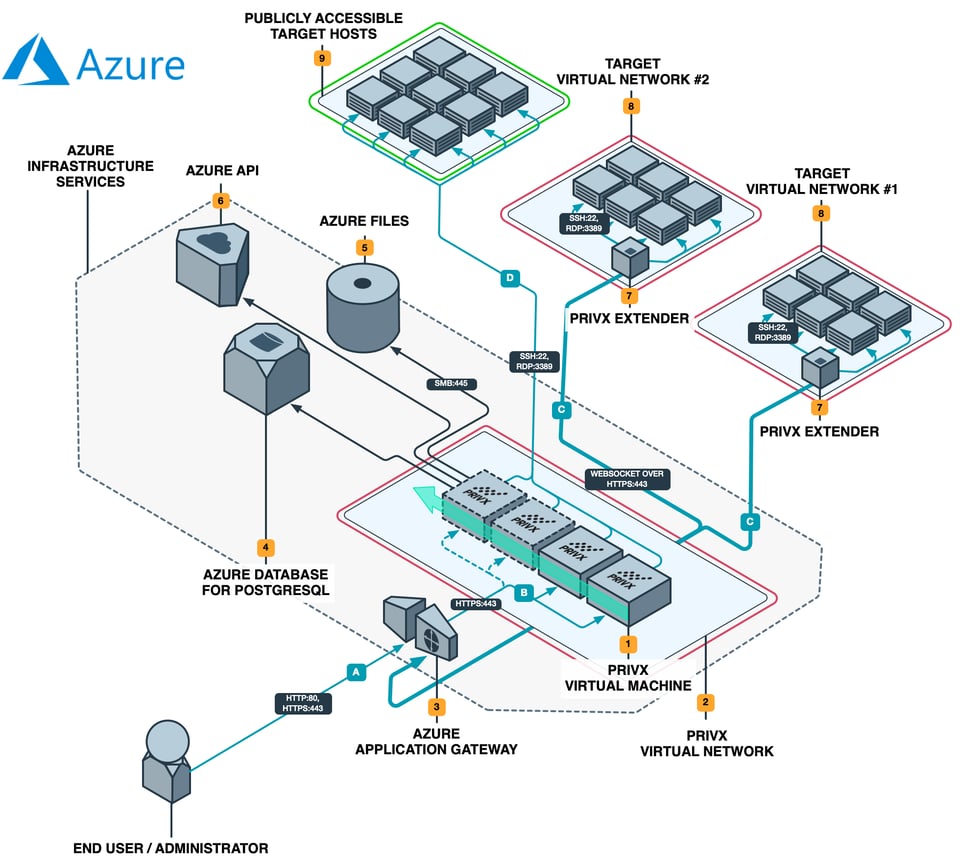
Peak Performance with Modern Architecture
-
Modern, cost-efficient micro-service architecture allows auto-scaling, high performance and agility
-
High availability, Zero downtime upgrades
-
Easy to deploy, multiple deployment options
-
Fast turnaround time to provisiong access in the cloud, on-premises or hybrid.
Easy to Use
-
Single sign-on (SSO) access with multiple options (biometric, passkey, MFA...)
-
Modern browser-based UI or command line tool
-
User Entity Behaviour Analytics (UEBA) for anomalous behaviour detection and prevention

See how PrivX PAM3 compares against traditional PAM solutions, like CyberArk or BeyondTrust.
PrivX
Learn more about PrivX

PrivX Data Sheet

Why The Future of Cybersecurity is Passwordless & Keyless

What should you look for in a PAM Solution?


