Tectia® SSH Client/Server Zero Trust Edition
Enhance your access control and auditing
Protect your critical access
for the future with Zero Trust
Tectia Zero Trust Edition protects and tracks all your interactive and machine-to-machine connections. It eliminates your static credentials, provides secure role-based access, and records full access logs.

Role-based access control (RBAC)
Grant access based on users' roles, rather than identity.
Tectia Zero Trust Edition integrates with your Identity and Access Management (IAM) system to ensure role-based access.

Detailed audit trails
Pass compliance audits easily.
Tectia Zero Trust Edition logs all user authorizations and activities in a centralized system that integrates with your SIEM.

Multi-protocol support
It's not just about SFTP anymore.
With Tectia Zero Trust Edition, you can grant access to your customers and collaborators also via their web browsers.
Typical challenges with file sharing
How to routinely and securely share files between internal networks or outside your organization?
How to securely handle data that is sensitive or critical to your operations?
How to implement strict control and auditing to gain visibility into who gets access to your files?
How to get high availability for your file sharing?
File sharing for heavy users
Centralized role-based access
Instead of direct server access, users are granted access based on their roles. A single role allows access to multiple servers at a time.
It is possible to grant temporary access. After a chosen time period is over, the granted access automatically expires.
Easy auditing and monitoring
Tectia Zero Trust Edition has a single, centralized activity log for your entire server estate. Users are always identified and all activities are tracked with detailed audit trails. All audit logs are tamper-proof.
Tectia Zero Trust Edition also supports SIEM integration for easy activity monitoring.
A complete feature package
Tectia Zero Trust Edition includes all features of the previous Tectia SSH Client/Server Edition as well as the Tectia Quantum Edition.
This way, Tectia Zero Trust Edition combines the strengths of classical encryption algorithms with the latest post-quantum algorithms.
Easy migration
Migration from an existing Tectia or OpenSSH Server is easy and straightforward. Our professional services team is ready to help if needed.
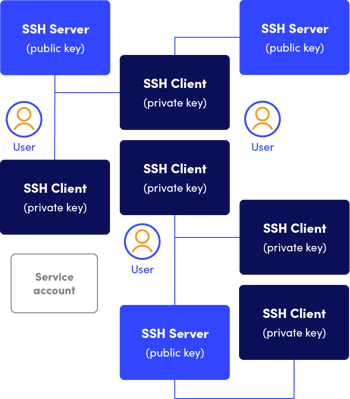
Before Tectia Zero Trust Edition
Imagine this set-up times 1000 - managing a server estate like that is not easy.
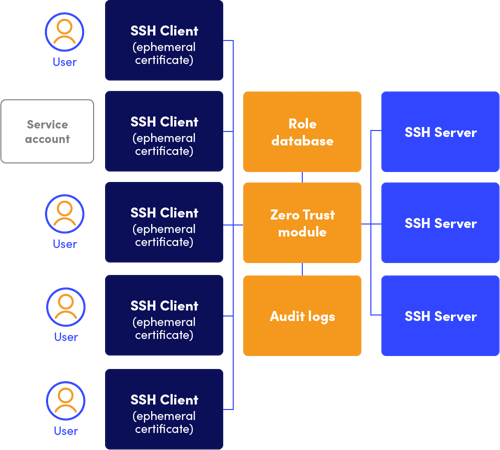
After Tectia Zero Trust Edition
Even with thousands of servers - your estate is organized and easy to manage with centralized access control.
Tectia Zero Trust Resources
Solution brief
Role-Based Access: Secure Access with Tectia Zero Trust
Learn about Tectia SSH Client/Server Zero Trust Edition and the technology behind the solution.
case study
Improved Security with Quantum-Safe Technology and Zero Trust Access Management
Learn how one of our customers secured and improved their access management and download center experience with Tectia Zero Trust Edition.
Zero trust solution portfolio
Zero Trust by SSH: Solution Portfolio
Tectia Zero Trust Edition is a part of a solution portfolio offering comprehensive protection for your data-in-transit, data-at-rest, and data-in-motion.


