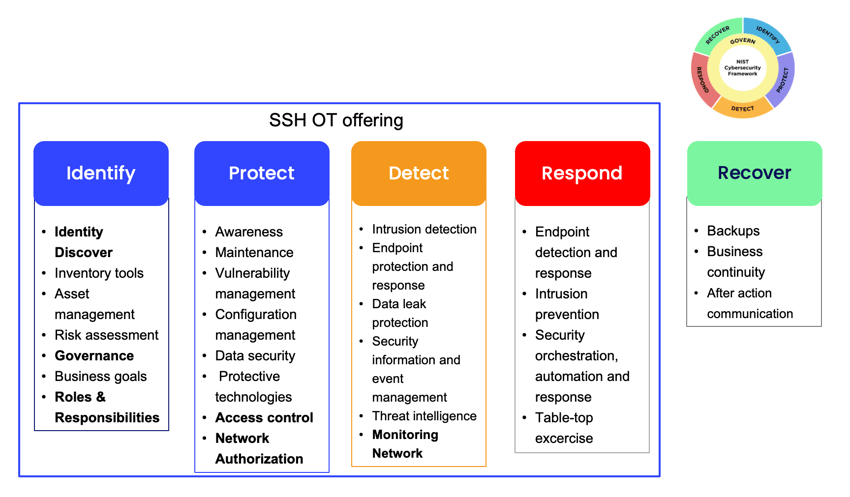
SSH OT offering fulfills NIST CSF 2.0 requirements
Our comprehensive OT security offering covers four out five main categories of the National Institute of Standards and Technology Cybersecurity Framework 2.0.
- Identify
- Protect
- Detect
- Respond
SSH OT Portfolio - Your best shot at securing OT infrastructures
Aligning with the Purdue model

- Our PrivX OT solution can be deployed on-site or as a shared instance across multiples sites or regions to a public or private cloud.
- The base of access is identity.
- Named users who are tied to the HR processes are imported to PrivX OT.
- The solution can integrate to any number of identity solutions.
- Or site-specific or local identity source giving controlled access to a wide range of employee identities
- The users are imported and mapped to roles - continuously .
- PrivX OT hosts the site's required access topography as a role structure. Examples:
- Production management roles access ERP
- Plant control oversees the production across multiple processes
- Process-specific roles granting access the supervisory or control roles
- 3rd party contractors are given just-in-time and time-boxed temporary access to specific resources
- without bringing the contractors to the organizational identity source
- letting contractors install their own proprietary connectivity solutions
- Usually, operational management stations in level 3 which provide secure access to control & monitor processes on lower levels.
- PrivX OT can be deployed outside the site and still reach destinations within the site to make the private, protected networks accessible.
- PrivX OT supports various mechanisms to authenticate to access management solution, including:
- standard identity provider SSO
- client certificates
- passkeys
- biometric authentication
- and more
- The connections can be audited, restricted to happen during working hours or from specific source addresses. The authentication to the target systems can happen via passwords, keys or passwordless, ephemeral access.
- With role based network access, log in to PrrivX OT and request routed network level access to a target system which enables them to use various OT protocols.
- PrivX OT can monitor for PAM bypassing connections and detect threats or vulnerabilities within the OT network.
Customer cases
Related resources
See the solution in action - book a demo!
Experience the functionality of PrivX OT Edition and see the future of
secure access control in OT!
Thank you for submitting your request. We'll get in touch with as soon as possible to arrange a time that suits you.


















