FTP – Use of SSH/SFTP Instead Recommended
Transferring files from computer to another is a basic requirement in any corporate network - doing so securely is a business necessity.
This page explains how you can migrate from the insecure FTP to a secure alternative – SFTP (Secure File Transfer Protocol).
Contents
FTP – Protocol and Application How Does It Work? Availability and Usage Inherently Insecure Popular Implentations and a Secure AlternativeFTP – Protocol and Application
FTP is an application and a protocol for transferring files and directories between computers over a data network. Mr. Abhay Bhushan wrote the original protocol specifications in the early 1970s. Since then FTP has gained wide acceptance by the general computing audience. The widely adopted protocol has been standardized by the Internet Engineering Task Force (IETF). The current standard is described in RFC 959.
How Does It Work?
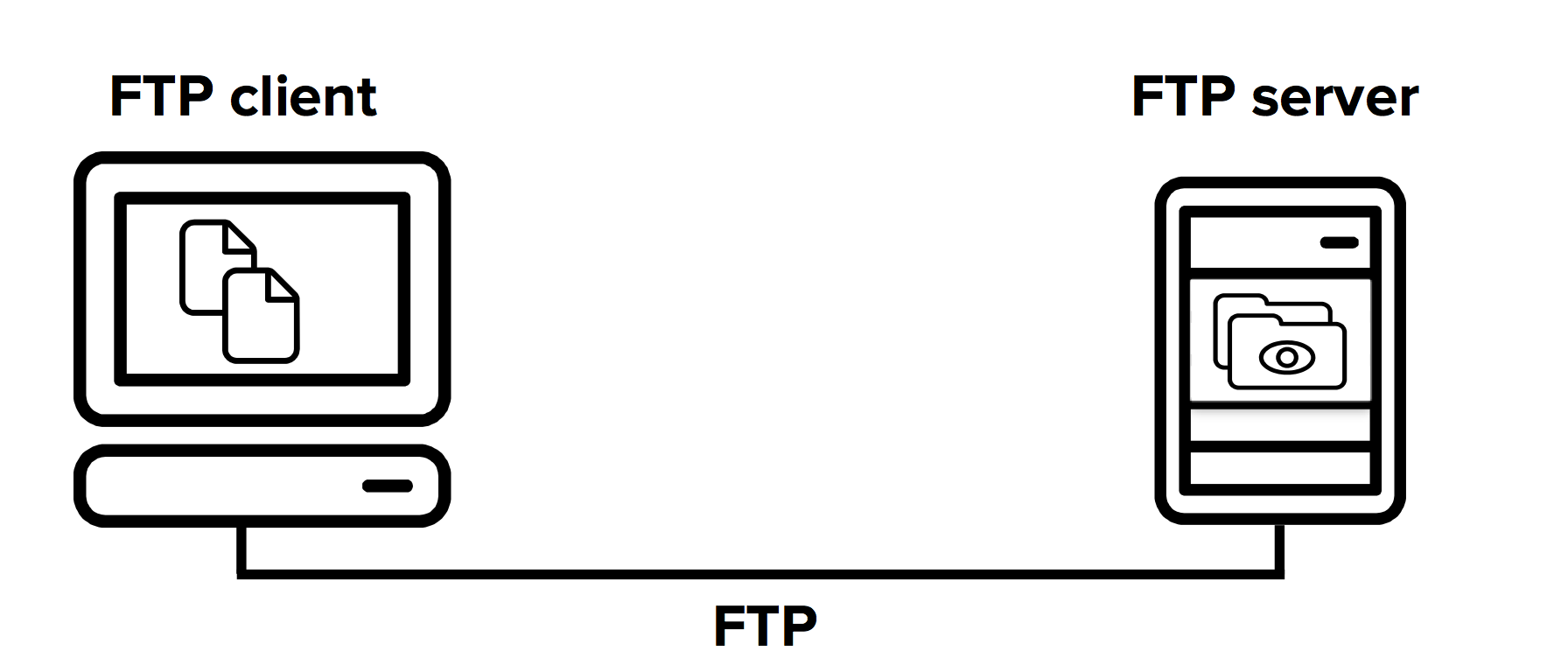
FTP is an application layer protocol and runs on top of the TCP/IP protocol. It works on a client-server model. This means that the file transfer connections are (usually) initiated by an FTP client and responded to by an FTP server. Once an authenticated connection has been established between the client and server, the files and folders can be transferred to either direction between the two connected computers.
Availability and Usage
FTP is one of the oldest data transfer methods in IP networks. Consequently, it has been included as a standard component in many operating systems. Most operating systems offer an FTP server, and client software is also widely available. There is a selection of client applications available for all common desktop operating systems.
The protocol used to be widely used by system administrators and software developers for moving files and folders from one computer to another. However, it has been largely replaced by SFTP due to security concerns, robustness issues (especially in relation to Network Address Translation (NAT)), and ease of use.
Inherently Insecure
When FTP was initially specified and designed, the importance of network security was less pronounced than today. The file transfer protocol was not designed to be secure – it offers no protection for the privacy nor integrity of the files that are transferred, nor does it protect the identity of the communicating parties. All passwords and data are transferred in the clear. These well-known and recognized security concerns for the protocol were addressed by the IETF in an informational RFC document RFC 2577. The protocol also does not work well over firewalls and address translation, which are very common in today's networks.
Because an eavesdropper can easily intercept user passwords and transferred data, the protocol should only be used in networks that are trusted. In non-trusted networks such as the public Internet, file transfers should be done with a secure alternative such as SFTP or SCP (Secure Copy Protocol). The SFTP protocol, for example, offers equivalent file transfer capability but is enhanced with protection of user identities, login credentials, and transferred data.
Popular Implentations and a Secure Alternative
The popularity of the FTP protocol and its many use cases have spawned a number of implementations of the protocol. Popular implementations are, for example, FileZilla and WinSCP for the Windows operating system.
Read more about FTP clients and FTP servers.

