Cool PAM with great auditing and easy access to IT assets in the cloud
2019 has been an exciting year for privileged access management (PAM): we’ve seen the rise of the Zero Trust framework, recommendations from Gartner analysts towards Just-In-Time (JIT) and Zero Standing Privileges (ZSP) models and our very own lean PAM - PrivX, has steadily evolved to accelerate the industry’s transition to JIT access.
Also, PrivX project has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No 881221.

Since introducing PrivX in 2018, our aim has been to develop a product that is not only secure, but one that also promotes a positive and practical experience.
Read on to discover how PrivX can bring that experience to your organization, be it in small and medium sized enterprises (SMEs), innovative and cloud-borne R&D teams in large organizations, or early-growth companies.
Privileged Access Management (PAM) in Modern IT Infrastructures
What is Privileged Access Management?
Privileged Access Management (PAM) is a critical cybersecurity strategy that controls and monitors the elevated access — or privileged access — granted to users, accounts, and processes within an IT environment.
It is designed to prevent security breaches by limiting the potential for unauthorized access to critical systems and data.
With PAM, organizations can effectively manage and audit the use of privileged credentials, ensuring that only the right individuals have the right access at the right time, and for the right reasons.
Go Beyond PAM Basics: Just-in-Time (JIT) and Zero Standing Privileges (ZSP)
Evolving beyond traditional PAM, just-in-time (JIT) and Zero Standing Privileges (ZSP) represent a shift toward a more dynamic and secure access management framework.
JIT ensures privileges are granted only as needed, significantly reducing the risk window and aligning access with specific tasks.
ZSP takes this concept further by ensuring that accounts do not retain privileges beyond their immediate task, effectively neutralizing the threat of dormant accounts being exploited.
These strategies are integral to a lean PAM approach, where efficiency and security converge to fortify IT infrastructures against evolving threats.
Benefits of Lean Privileged Access Management with PrivX
PrivX™ Hybrid PAM Solution by SSH is an innovative PAM tool that embodies the essence of lean and efficient security. PrivX revolutionizes PAM by delivering a solution that simplifies access to IT assets in the cloud while ensuring comprehensive auditing capabilities.
With PrivX, organizations benefit from streamlined access workflows that enable secure, passwordless authentication and just-in-time access to credentials. This ensures users have immediate access to the resources they need without the risks associated with permanent privileged accounts.
Additionally, PrivX's robust auditing features provide detailed access logs and session recordings, making it easier to meet compliance demands and detect potential security incidents.
Key Features of PrivX that Make PAM Easier
1. Always-on logging
Provide continuous monitoring of critical assets with always-on logging. This feature records all user activity on every connection established to the asset, ensuring comprehensive audit trails.
You can replay recorded sessions, view connection metadata, session-specific audit events, and files transferred.
There's also keyword search within SSH and SFTP connection transcripts, enhancing the capability to scrutinize access logs, ensuring multi-factor authentication and strong oversight of SSH connections.
2. Visibility only to authorized resources
Ensures visibility only to authorized resources by implementing a need-to-know model. This access management solution verifies and authorizes the identity of all personnel before granting access to specific resources, promoting role-based access control and improving security.
This model helps maintain a Zero Trust access framework, aligning with the highest standards of privileged access security. Organizing users into identity groups ensures that access is tightly controlled and monitored, further protecting sensitive information.
3. JIT access with ZSP to cloud & on-prem
Support just-in-time (JIT) access and Zero Standing Privileges (ZSP) for both cloud and on-prem environments. This means granting one-time access to only the required target systems or applications, ensuring no privileged access exists prior to or after the access has expired.
This approach reduces the risk window and adheres to Gartner’s recommendations for a Zero Trust authentication framework, making access both secure and efficient for privileged users.
4. Granular access control
Granular control over SSH and RDP traffic, restricting access to specific channels and limiting it to a particular application on your Windows target system when necessary.
This precise level of control is crucial for maintaining secure communications and effective access governance, ensuring that only the right individuals have the right access at the right time.
5. Safe use of shared accounts
Allow safe and auditable use of shared accounts for accessing management consoles or target systems. This is achieved without exposing credentials to individual users, ensuring robust audit trails, and maintaining high standards of privileged access security.
Shared accounts can be a challenge in access management, but this is handled seamlessly by utilizing a secrets vault for secure credential storage.
6. Monitor audit events using SIEM & cloud log collectors
Integrate PrivX with existing monitoring dashboards in external systems such as Splunk, AWS CloudWatch, or Azure Event Hub. This allows for real-time monitoring and triggering of alerts based on PrivX audit events.
SIEM and cloud log collectors enhance your organization’s ability to detect and respond to potential security incidents promptly.
7. Connect to VPCs securely without additional hardware/software costs
PrivX Extender, an add-on component, facilitates secure connections to resources in your Virtual Private Cloud (VPC) without incurring additional hardware or software costs.
This feature extends JIT access with ZSP to VPCs, ensuring secure and cost-effective management of cloud resources, a vital aspect for modern cloud architects and IT professionals.
8. Native-client friendly
Let your end-users continue using native SSH and RDP clients while retaining all the above benefits of provisioning access via PrivX.
This compatibility ensures seamless integration and user experience, leveraging single sign-on (SSO) for quick and secure access authentication. Based on assigned roles and identity groups, users can easily list and connect to allowed targets, maintaining efficient and secure operations.
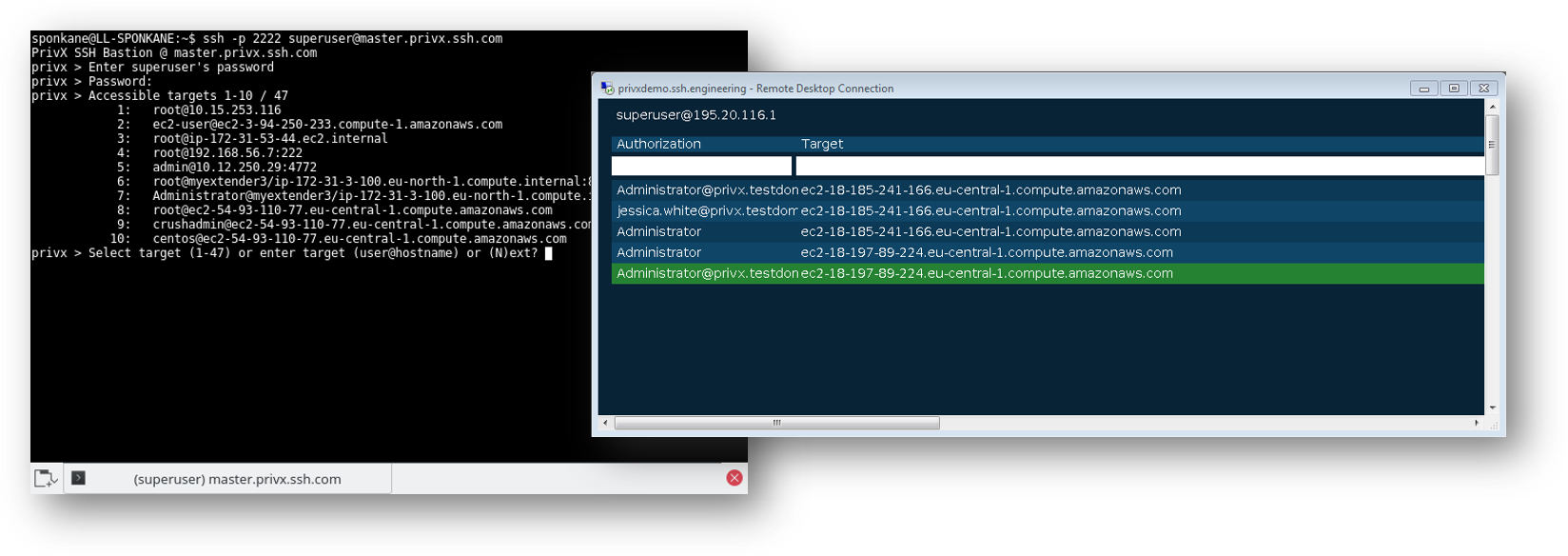
9. Time to value - One-click, agent-less access to target hosts
Every authorized resource is just one-click away in the PrivX UI with the browser-based SSH & RDP connectivity, along with access to web apps, significantly improving the net promoter score among users.
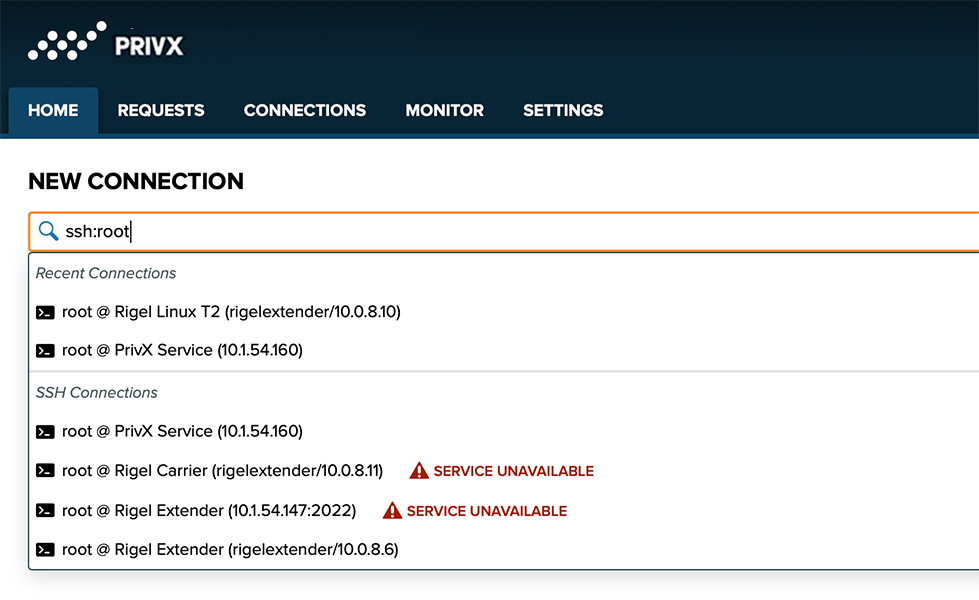
With the introduction of a search field in the PrivX home screen, starting connections to authorized resources gets even easier, especially in environments with hundreds or thousands of hosts.
Search within allowed/available targets using protocol, host name, user account or tags and see the status of the service availability right from the search results.
Embrace the Future of PAM with PrivX: Get the latest software for free
PrivX is designed to meet the evolving needs of access management in the digital world. Whether you are part of a global manufacturing business, an innovative R&D team, or an SME, PrivX provides a robust and user-friendly access management solution.
Adopting lean principles and advanced security features like JIT access, ZSP, and role-based access control, PrivX helps organizations achieve secure and efficient access management.
If you’ve read this far, we’ve likely raised your curiosity about PrivX. So why don’t you take it for a test drive? We offer the full product experience in a browser - with nothing to install - Test Drive Now.
Take advantage of PrivX’s powerful features to enhance your organization's security posture, streamline access workflows, and ensure compliance with industry standards. Test drive PrivX today and experience the future of privileged access management.
FAQ
What is session recording and how does it enhance cybersecurity?
Session recording in PrivX ensures all user activities are logged and monitored in real time. This provides an audit trail to identify unauthorized or suspicious activity, enhancing cybersecurity for wholesale companies, retail companies, and events companies. Session recording supports the Zero Trust framework by ensuring visibility and accountability in multi-cloud environments, essential for maintaining robust security.
How does PrivX support passwordless authentication in a hybrid PAM environment?
PrivX enables passwordless authentication, reducing credential theft risks. Supporting just-in-time (JIT) access and Zero Standing Privileges (ZSP), PrivX ensures users only have access when necessary, enhancing security.
What makes PrivX a patented PAM solution with great new features?
PrivX is a patented PAM solution recognized by industry analysts for its innovative features like session recording, passwordless authentication, and granular access control. It supports password vaulting and encryption keys, ensuring secure credential management for SMEs and large organizations.
How does the Zero Trust framework integrate with PrivX for secure access?
PrivX incorporates Zero Trust, continuously verifying and authorizing access; supports JIT access and ZSP, minimizing unauthorized access risks, even in multi-cloud environments, aligning with industry standards.
Where can I find a white paper, buyer's guide, or analyst report on PrivX?
You can find comprehensive resources such as white papers, buyer's guides, and analyst reports on PrivX on the official SSH.COM website. These documents provide detailed insights into the capabilities and benefits of PrivX, making them valuable resources for companies seeking to improve their organization's security posture.
How does PrivX fit into a bigger ecosystem with SSO and GSuite integration?
PrivX integrates seamlessly with SSO and GSuite, streamlining authentication for companies like Efavormart in Bell Gardens, United States. This enhances productivity and security, supporting automated applications and quantum-safe connections, and ensuring a secure, future-proof IT infrastructure.
Esa Tornikoski
Esa Tornikoski is Product Manager for PrivX and Crypto Auditor products. Esa joined SSH late 2017. Prior SSH he has been working in Product management roles at Telecom and IT security companies (Elisa, F-Secure and Siemens). He has a Master of Science degree in Computer Science from Lappeenranta University of...
