Universal SSH Key Manager has evolved into PrivX Key Manager
Centralize and automate your
key management
with Zero Trust
Secure your business with a proven Zero Trust key(less) management solution. Discover and manage all your SSH keys and accounts to mitigate risks. Reduce complexity with automation features. Never fail an IT audit again due to unmanaged SSH keys.
Key management and PAM join forces!
Discovery, centralized secrets management, policy reporting, and migration to passwordless and keyless authentication are now all under one hood.
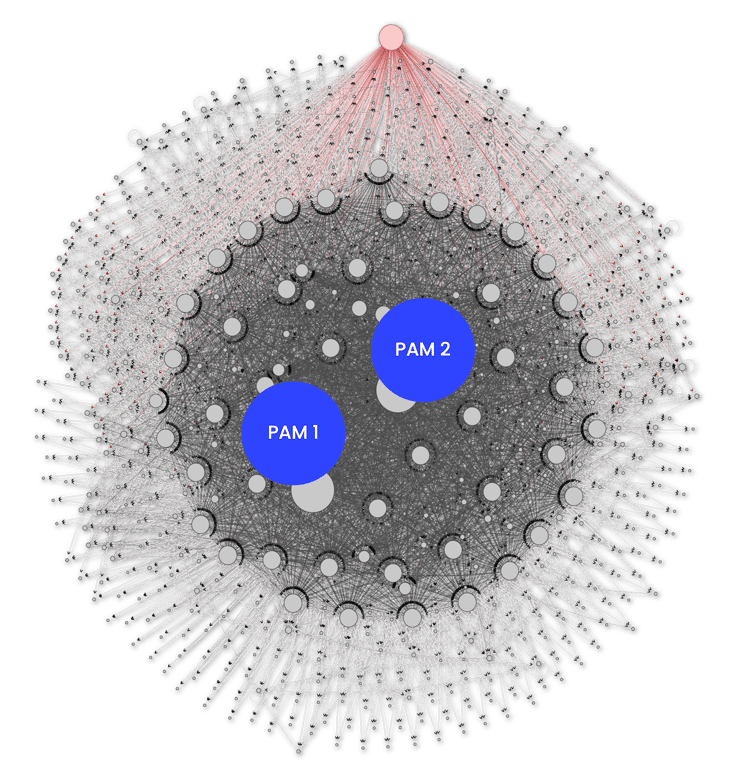 80% of your critical credentials might be
80% of your critical credentials might be
out of control
SSH keys are credentials just like passwords but 10 times more common and unmanaged. We scanned a financial institution's environment. That death star is the result. Their Privileged Access Management (PAM) security controls were being bypassed with unauthorized, test-to-production, and application-to-application connections.
How did we remedy the customer's situation?
No ID
SSH keys don't have an identity associated with them. We changed that.
Never expire
Keys don't have a best-before date. We gave them that.
One to many
One key can open connections up to hundreds of targets. We put a stop to it.
Old PAMs can't handle them
Old PAMs handle 20% of all keys - at best. We manage them all
Stop security control bypass for true access closing

1. Eliminate SSH key risks and attack vectors
SSH keys are complex and can easily go unmanaged. These unmanaged SSH keys are then highly sought after by malicious actors.
With PrivX Key Manager, you remove security risks caused by ungoverned keys that might look legitimate to your existing security controls.

2. Centralize & automate SSH key lifecycle management
By default, SSH key management is decentralized and complex.
With PrivX Key Manager, you manage and discover all authentication keys, key configurations, and SSH login files in a centralized, universal SSH key manager. You can also automate SSH key processes, like provisioning, rotation, remediation, etc.
Compare SSH key management using PrivX Key Manager VS CyberArk >>>

3. Secure and track your encrypted M2M connections
Machine-to-machine connections are not managed by PAM tools. You need a centralized SSH key management tool, like PrivX Key Manager, to manage your M2M connections, automate routines, track machine credentials, and audit all automated sessions.
PrivX Key Manager also ensures that all M2M connections meet your security policies and use compliant encryption standards and protocol versions.
Learn about the best practices for securing machine credentials in our whitepaper >>>

4. Enforce security policies and pass IT audits
PrivX Key Manager warns you about SSH keys that violate your policies, contravene regulations, or are used ungoverned. You can upgrade, rotate, and delete outdated keys with the option to reverse any action.
With PrivX Key Manager, you enforce compliant access control policies throughout your entire organization.

5. Reduce complexity with Zero Trust keyless access
With PrivX Key Manager, you can maximize key lifecycle automation and radically reduce the number of SSH keys in your environment.
PrivX Key Manager grants only just enough access (JEA), just-in-time (JIT), and with the least privilege needed to get the job done - without leaving any SSH keys behind to manage.

6. Choose zero-touch SSH access governance
PrivX Key Manager makes it easy to manage your SSH keys. You can manage authentication keys in their native locations without complicated vaulting onboarding processes.
PrivX Key Manager comes with non-intrusive deployment without changes to the SSH configuration files, your existing key architecture, or application code.
The proven centralized SSH key management in 5 steps
PrivX Key Manager is a Zero Trust SSH key management solution that automates the governing
of SSH keys according to compliance and security standards.
PrivX Key Manager mitigates risks, reduces key management complexity, helps pass IT audits, and allows migrations to keyless access.
 Discover
Discover
Scan your environment and discover all SSH access (automated and interactive) across your IT infrastructure. Identify trust relationships and all policy-violating SSH keys. Discover different types of accounts.
Audit
Implement systematic company policies. Monitor and control your environment via centralized SSH key management.
Remediate
Remediate your environment. Remove keys that are uncompliant, unmanaged, or bypassing your controls.
Automate
Automate the full lifecycle of SSH keys and simplify the effort of staying compliant. Ensure all your sessions are audited, logged, and tracked.
Migrate
Radically reduce the overhead of managing permanent SSH keys and move to keyless, just-in-time Zero Trust access with short-lived certificates.
NPS = 71
Our customers love PrivX Key Manager!
Thanks to our customers, we have a Net Promoter Score (NPS) score of 71 for our PrivX Key Manager, a centralized SSH key management solution.
SSH is the perfect partner for us and we work very well together. The progress we have made over the past 4 years has been amazing.
Global top 10 bank IT architect
We have a very good working relationship with SSH. When we have a new issue, they are able to do that quickly. When we need something, they listen.
PrivX Key Manager customer
PrivX Key Manager is very stable. It’s easy to use once you understand the concept.
PrivX Key Manager enterprise user
Start your journey toward modern SSH key management
Discover the full scope of your SSH keys-related risk and prepare for an IT audit
Our SSH Risk Assessment is a complete assessment process that helps you discover all your SSH keys, servers, accounts, and related risks. Take back control over your environment with detailed reports and recommendations from our experts.
Compare the different PrivX Key Manager editions
Choose the best fitting PrivX Key Manager edition to manage your SSH keys.
| Capability | Analyze | Comply & Automate | Zero Trust |
|---|---|---|---|
| User Interface authentication with Windows AD, LDAP, SAMLv2 |
●
|
●
|
●
|
| High availability |
●
|
●
|
●
|
| User account inventory |
●
|
●
|
●
|
| SSH Key inventory |
●
|
●
|
●
|
| Trust relationship mapping |
●
|
●
|
●
|
| SSH key usage |
●
|
●
|
●
|
| SSH access discovery (password/key/certificate) |
●
|
●
|
●
|
| Compliance validation: NIST, HIPAA,PCI-DSS, etc. |
●
|
●
|
●
|
| Compliance reporting |
●
|
●
|
●
|
| User key management: removal, rotation, provisioning, hardening | - |
●
|
●
|
| Elimination of self-provisioning SSH keys | - |
●
|
●
|
| Application-based visibility and control of user keys | - |
●
|
●
|
| Capability | Analyze | Comply & Automate | Zero Trust |
| Hostkey rotation and distribution | - |
●
|
●
|
| SSH client/server configuration management | - |
●
|
●
|
| Rest APIs | - |
●
|
●
|
| GUI automation flows | - |
●
|
●
|
| SSH access with Keyless, Certificate-based JIT authentication | - | - |
●
|
| SSH access with AD, OpenIDC, or LDAP authentication | - | - |
●
|
| SSH access with Multi-Factor Authentication (MFA) | - | - |
●
|
| Virus scanning and file validation on file transfers | - | - |
●
|
| Centralized SSH connection control | - | - |
●
|
| SSH session recording | - | - |
●
|
| SSH auditing with SIEM integration | - | - |
●
|
| SSH sub-protocol control, e.g. allow/deny SFTP/x11-forwarding | - | - |
●
|











