Identity-focused PAM
Identity-based authentication & privileged access management
The power of one:
IAM & PAM & workflow approvals
The convergence of IAM and PAM offers a comprehensive approach to managing identities, access, roles, and approval workflows with monitoring and auditing to ensure smooth operations and regulatory compliance.
Strong identity-based security and access management
By combining IAM and PAM into a unified solution, we can now utilize their complementary capabilities in the battle against modern sophisticated cyberattacks. Together with Appmore, we created a powerful platform that:
-
combines IAM’s identity and access governance (MFA, SSO, etc.) and entitlements
-
PAM's RBAC, access monitoring, session recording, and auditing
-
ticketing and approval workflows with native integration to ServiceNow
Request and grant access based on roles
Role-based access control (RBAC) is enabled by our PrivX PAM based on the roles automatically provisioned by Appmore's integrated IAM. Users can easily request access, which is then granted automatically based on their role's permissions. Admins can easily grant temporary or permanent access based on a task, project, etc.
Seamless workflow approvals
Utilize automatic support for the joiner-mover-leaver process, including third parties. When employees join, move, or leave projects within the organization as per HR processes, this approach ensures that access is granted, modified, or revoked as necessary.
Ensure compliance with regulatory requirements
All actions, such as request, add, grant, and remove, are traced and logged which makes recertification of the roles a natural part of the solution. This ensures that the privileged and other rights meet the roles granted to the specific user(s) and follow regulatory requirements.
Minimize the risk of unauthorized access
The solution automatically detects anomalies in sessions (e. g. PAM bypass) and reports them. In case of company policy violation, the solution automatically revokes access - even if users have otherwise valid credentials.
Fulfill the requirements for the Segregation of Duties (SoD)
This can prevent, for example, test-to-production access or payment and approval of an invoice being granted to the same person. This is a fundamental requirement for many regulatory standards and processes, such as PCI DSS.
Enable end-to-end passwordless authentication
Grant passwordless access just-in-time for the session without users ever seeing or handling the secrets needed to establish the connection. Use methods like biometric authentication and single sign-on (SSO) to build a passwordless path for your users. It’s convenient, secure, and efficient.
How does it work?
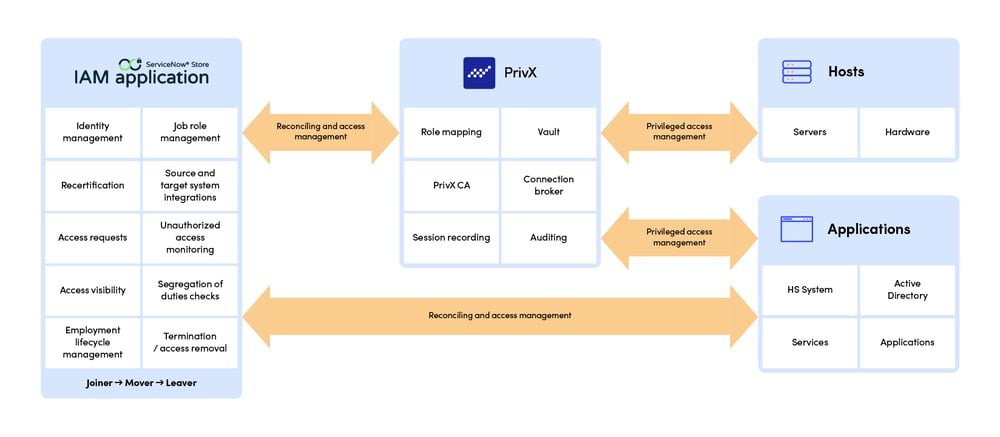
1. Access requests and granting
Users can request access via Appmore's ServiceNow application, and admins can easily grant access based on roles.
The application eliminates the need for email or other legacy solutions for handling access requests. HR can integrate their joiners, movers and leavers process with identity and (privileged) access management.
2. Passwordless authentication
When possible, users can utilize passwordless authentication methods, like biometric authentication. When needed, credentials like passwords and keys can be still used, vaulted, rotated, and managed appropriately.
3. Access monitoring and compliance
The solution provides the necessary tools to comply with access requirements of regulations such as GDPR, ISO27K1, and PCI DSS.
Access is automatically revoked when anomalies occur during a session, for example, if the antivirus solution is disabled.
4. Automatic access revocation
When an employee's tenure ends, the IAM application manages the inactivation of users' accounts and the removal of all access rights. Since PAM is synced with IAM, all access privileges are revoked at the same time.
Additionally, all actions, such as request, add, grant, and remove, are traced, and logged.
legacy
 Perimeter security
Perimeter security
modern
 Hybrid cloud
Hybrid cloud
Vaults and keyless
Firewalls/VPNs and Zero Trust
best-in-class
 Zero Trust
Zero Trust
Keyless + passwordless
Automated + immutable
the future of ssh access and credentials management
Get the 'Future is passwordless and keyless' white paper
Manage both passwords and SSH keys with least management effort and with minimal number of always-on credentials. No complex management solutions. Reduced management overhead. All Zero Trust and just-in-time aligned. Fill in the form to get your copy >>>

Thanks for submitting the form.

