
- Solutions
- SOLUTIONS
- PrivX Zero Trust Suite
- SalaX Secure Collaboration
- Strong ID-based access with Entra ID & Zero Trust Suite
- Quantum-Safe Cryptography (QSC)
- Security Risk Assessment, Quantification & Mitigation
- OpenSSH by SSH
- Device trust & access and identity verification
- Identity-based authentication & converged IAM and PAM
- TOPICS
- INDUSTRIES
- SOLUTIONS
- OT Security
- Products
- Services
- Customer cases
- Resources
- Solutions
- SOLUTIONS
- PrivX Zero Trust Suite
- SalaX Secure Collaboration
- Strong ID-based access with Entra ID & Zero Trust Suite
- Quantum-Safe Cryptography (QSC)
- Security Risk Assessment, Quantification & Mitigation
- OpenSSH by SSH
- Device trust & access and identity verification
- Identity-based authentication & converged IAM and PAM
- TOPICS
- INDUSTRIES
- SOLUTIONS
- OT Security
- Products
- Services
- Customer cases
- Resources

Privx OT
Full-Scale Secure Access Control for Operational Technology
Centralize local, global or remote secure access management
to any IT/OT target at scale with the cost-efficient PrivX OT Edition software solution.


ICS and Production Site Protection
Why PrivX OT?
Secure Remote Access
On-site or off-site, locally or globally, for internal or external users, PrivX secures access in a uniform fashion and beyond mere remote access.
Passwordless ZSP & workflow process
Mitigate credential risk with passwordless authentication for Zero Standing Privileges (ZSP). Workflows ro authorizations and job approvals are built.in.
Patch management & secure file transfers
With built-in file uploads, uploading files to servers or patching ICS/OT targets is secure, easy and fast.
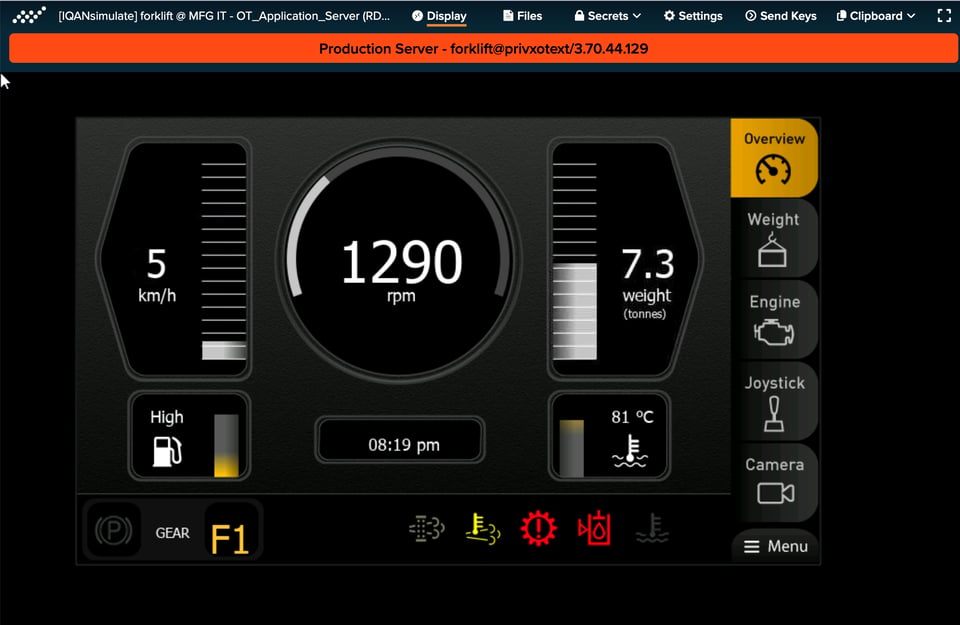
Maintain and troubleshoot remotely
-
Maintain, upgrade & optimize operations off-/on-site
-
Instant access for troubleshooting
-
Strong biometric authentication and device trust-based access to production sites
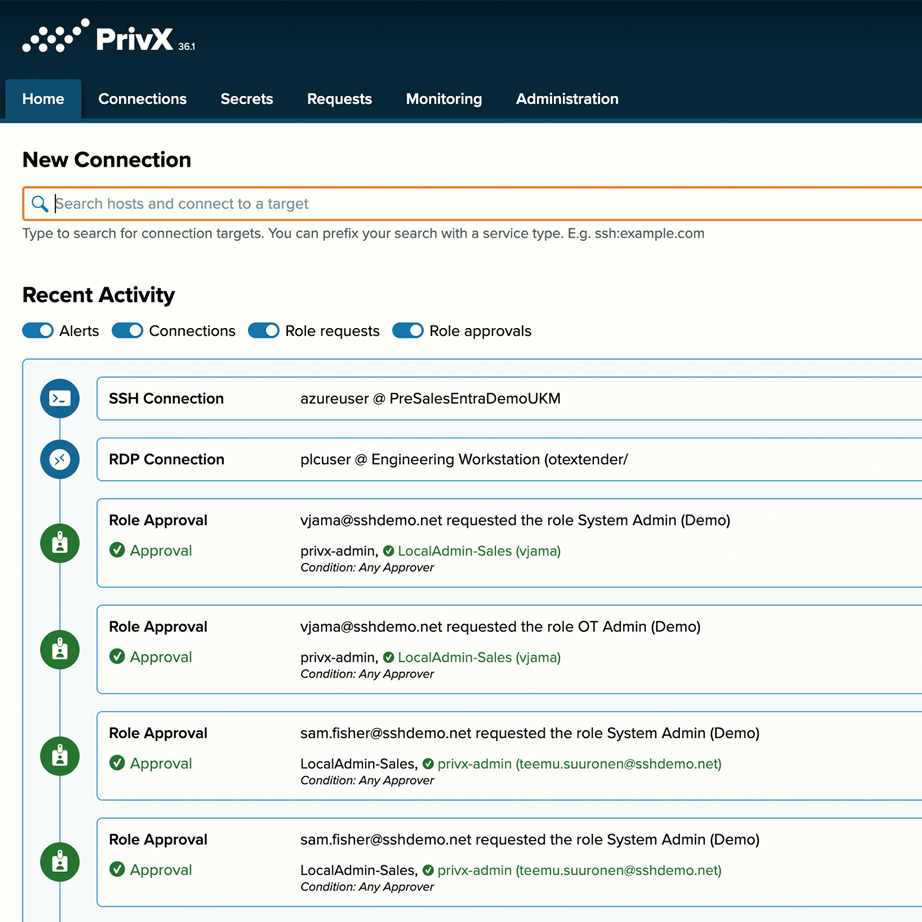
Centralized control
-
Access hundreds of machines or other critical IT/OT targets from a single digital gatekeeper
-
Work with multiple directories or IDMs and map them with the right roles for role-based access control (RBAC)
-
Audit trails, session recording, and monitoring for compliance (NIS2, IEC 62443)
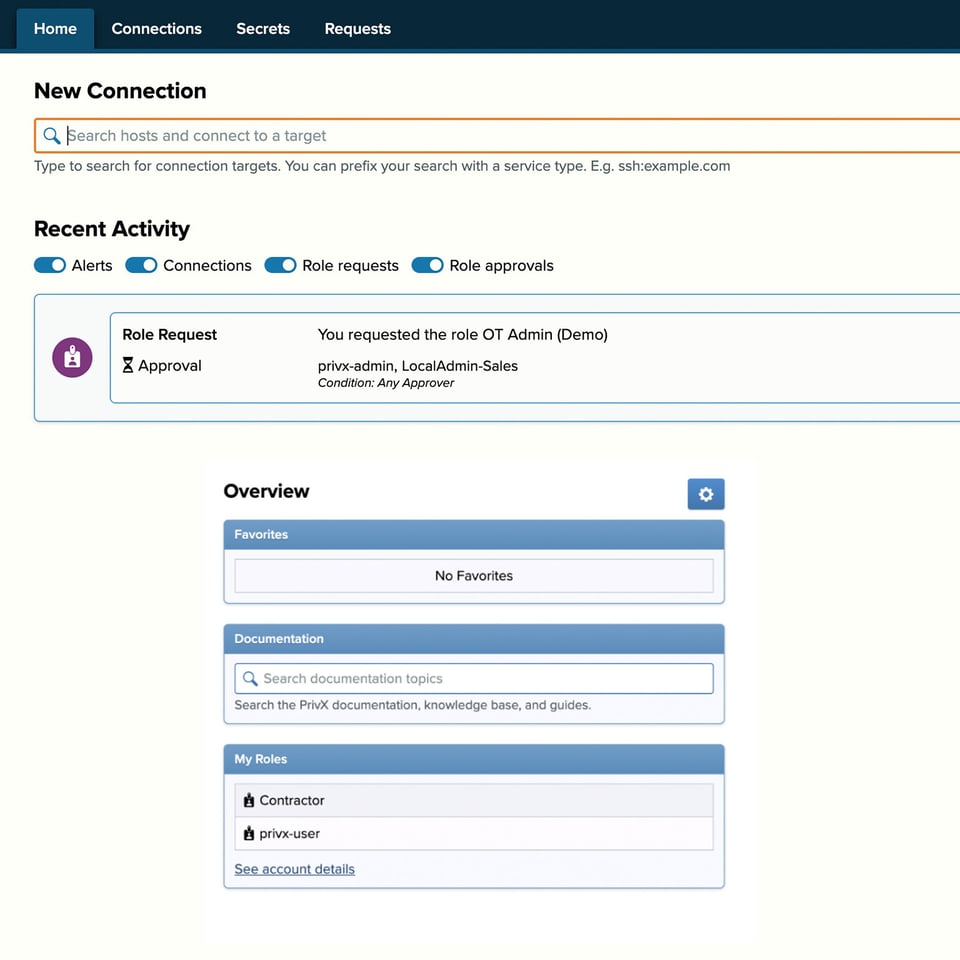
Approve, restrict, authorize
-
Workflows for job approvals or integrations to ticketing systems
-
Restrict the access to the minimum to get the job done
-
Manage credentials and migrate to passwordless and keyless authentication for efficiency and true Zero Trust security

Save on costs
-
Scalable, flexible, and easy to deploy: No costly hardware
-
Uniform access using industrial protocols or standard IT protocols (SSH, RDP, VNC, HTTP(S), Profinet, EtherNet/IP, Modbus, OPC UA, and more)
-
Software from leading security experts with a strong footprint in demanding projects in OT, banking, healthcare, and MSPs


A Marine Vessel Operator Secures Remote Access for 1000s of ships for Diagnostics and Maintenance

Manufacturer in Forest Industry Secures Global and Local Access to Sites
PrivX OT for ICS security
See PrivX OT in Action
Multiple access methods using any protocol
-
three types of access methods for connections between users and network devices
-
remotely or on-site
-
Network Target Access (NTA) supports industrial communication protocols between the user and target
-
without a local computer/jump host/vendor-specific applications
Secure File Transfer
-
file transfers between the user’s computer and the target device
-
no additional software, application upgrades or configurations for patch management or troubleshooting
-
highly intuitive and simple to use
-
integrates seamlessly with various anti-virus or malware check software
Access Request/Approval
-
enforces Zero Trust, Just-in-Time (JIT), Just Enough Role-Based Access
-
users only connect to devices based on an assigned role, for a specific amount of time and limited to the approved network target(s)
-
requesting and approving access is straightforward, takes place in real-time, and multiple UIs are available for communication, including a smartphone app.
Session Logging, Recording, and Real-Time Monitoring
-
get a total visibility into each user’s connection to systems and networks
-
log all connections, record session videos, and monitor users in real time as they access devices and other targets
PrivX OT
Go beyond remote access in IT/OT convergence
See how PrivX OT is the most comprehensive OT secure access solution on the market.
| SSH | BeyondTrust | Wallix | Claroty | Cyolo | Xage | |
|---|---|---|---|---|---|---|
| Account and asset discovery | ||||||
| Secure remote access | ||||||
| Passwordless | ||||||
| File and data transfer security | ||||||
| Fine-grained access control | ||||||
| SSH key management | ||||||
| Quantum-safe | ||||||
| Auditing and monitoring |
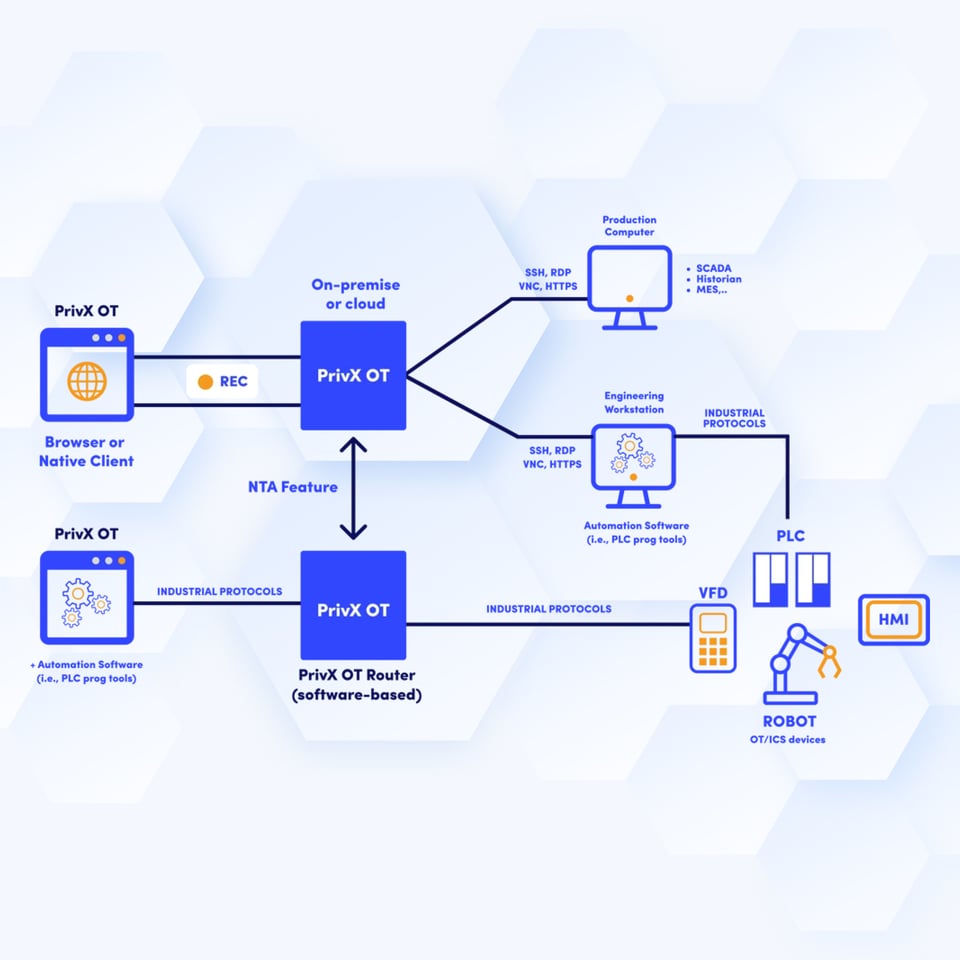
How does PrivX OT Edition work?
With IT/OT convergence, site engineers, administrators, maintenance personnel, remote operators, and consultants access industrial control systems (ICS) targets, including:
-
Programmable Logic Controllers (PLC)
-
Supervisory Control and Data Acquisition (SCADA)
-
Distributed Control Systems (DCS)
-
Human-machine Interfaces (HMI)
-
Remote Terminal Units (RTU)
PrivX OT Edition governs, identifies, authorizes, approves, audits, and monitors access to these resources in a secured and restricted manner. All while keeping your organization compliant with regulations.
Learn more about PrivX OT

Secure Remote Access Lifecycle Management for Operational Technology (OT)
Buyer's Guide.

Secure Access for Operational Technology (OT) and Critical Infrastructure
White Paper.

OT cybersecurity talk: Risk management, productivity optimization, OT security and safety
Webinar recording.